Active Directory (AD) underpins many contemporary IT environments by managing user accounts, computers, and permissions. Monitoring and auditing user login history in AD is essential for maintaining security, ensuring compliance, and diagnosing potential issues within an organization.
This article will walk you through viewing Active Directory user login history and auditing logon and logoff data. We will cover different techniques and tools for accessing and interpreting these logs, helping you effectively monitor user activity and maintain a secure and compliant IT environment.
Understanding Active Directory Login History
Active Directory User Login History is a record of user login and logoff events within an Active Directory environment. It provides valuable insights into user activity, security events, and troubleshooting.
Here’s an overview of some of the various types of AD user login history:
- Successful Logins Records instances where users successfully logged into their accounts.
- Failed Logins Logs unsuccessful login attempts, including invalid credentials or lockout events.
- Logoff Events Logoff events help in monitoring when and how users end their sessions
- Password Changes Tracks password changes and resets.
- Account Logon Events Account logon events provide details about authentication attempts at the domain level, including initial logon and subsequent authentication attempts.
- Account Lockouts Records when user accounts are locked due to failed login attempts.
- Network Logon Events Network logon events capture user logons performed over a network connection.
- Logon/Logoff Summarization and Reports Summarizing and reporting on logon and logoff activities helps in visualizing patterns and trends.
- Group Membership Changes Monitors changes in user group memberships.
- Object Access Events Tracks access to specific AD objects (e.g., files, folders).
By analyzing these types of login history, administrators can identify security threats, troubleshoot issues, and ensure compliance with organizational policies.
Configuring Active Directory for Auditing
Now let’s explore how to set up auditing in Active Directory. We’ll go over how to enable auditing using Group Policy, configure advanced audit settings, and check that everything is working as it should. By carefully following the steps below and configuring auditing settings in Active Directory, administrators can gain valuable insights into user activities and system changes:
Enable Auditing in Group Policy
1. Access Group Policy Management: Open the Group Policy Management Console (GPMC) on a domain controller or a machine with administrative privileges:
- Go to Start > Administrative Tools > Group Policy Management.
- Alternatively, type gpmc.msc in the Run dialog box and press Enter.
2. Edit the Default Domain Policy or Create a New GPO: Choose an existing Group Policy Object (GPO) or create a new one to configure auditing settings.
- Navigate to the desired GPO under Group Policy Objects.
- Right-click the GPO and select Edit.
3. Navigate to Audit Policy Settings: Configure the specific audit policies to monitor logon and logoff events:
- Go to Computer Configuration > Policies > Windows Settings > Security Settings > Local Policies > Audit Policy.
- Here, you will find various audit settings that can be enabled or configured.
4. Configure Audit Policies: Set policies for auditing logon events, account management, and other relevant activities. Here are the settings to configure:
- Audit Logon Events: Enable both Success and Failure to track successful and failed logon attempts.
- Audit Account Logon Events: Enable this to audit logon events at the account level.
- Audit Account Management: Track changes to user accounts, such as creation, deletion, and modification.
5. Apply the GPO: Ensure the GPO is applied to the relevant Organizational Units (OUs) or domain controllers:
- Link the GPO to the appropriate OU or domain within Group Policy Management.
- Force a Group Policy update by running gpupdate/force on the target machines or waiting for the next policy refresh cycle.
Setup Advanced Audit Policy Configuration
1. Access Advanced Audit Policy Configuration: Advanced Audit Policy provides more granular control over what is logged: Follow the following steps to access it:
- Go to Computer Configuration > Policies > Windows Settings > Security Settings > Advanced Audit Policy Configuration > Audit Policies.
2. Configure Detailed Audit Policies: Define specific audit policies to capture detailed events. Here are the policies to define:
- Logon/Logoff: Configure policies for detailed logon and logoff event tracking, including account logon, logoff, and special logon types.
- Account Logon: Track events related to authentication and account access.
3. Audit Policy Subcategories: Configure subcategories for more precise auditing. Here are examples:
- Logon/Logoff: Includes events like logon attempts, logoff, and account lockout.
- Account Management: Includes changes to user accounts, password resets, and group membership modifications.
4. Deploy the Settings: Apply the advanced audit settings to the target machines and domain controllers:
- Ensure that the audit policies are correctly deployed by using Group Policy Management.
- Verify settings through Event Viewer to confirm that the intended events are being logged.
Verify Configuration:
- Check Event Viewer: After configuring auditing, use the Event Viewer (eventvwr.msc) to verify that auditing settings are working as expected.
- View Generated Audit Logs: Navigate to Windows Logs >> Security to view the generated audit logs.
Viewing User Login History
After configuring Active Directory auditing, the next step is to view and audit user login history, including logon and logoff data, to make sure you’re monitoring effectively and can respond to incidents. You can do this using several methods: the built-in Event Viewer, PowerShell, and third-party tools. Below, you’ll find a detailed guide on how to use each method to view and audit user login history:
Using Event Viewer
1. Accessing Event Viewer: Event Viewer is a built-in Windows tool that allows you to view and analyze logs from various sources, including Active Directory. Here are the steps:
- Open Event Viewer by pressing Windows + R, typing eventvwr.msc, and pressing Enter.
- Alternatively, search for Event Viewer in the Start menu.
2. Navigating to the Security Log: The Security log contains records of security-related events, including logon and logoff activities. Here are the steps:
- In Event Viewer, expand Windows Logs and select Security.
- This log displays all security-related events, including logon and logoff events.
3. Filtering Logon and Logoff Events: Filtering helps you focus on specific events of interest in narrowing down the results. Here are the steps:
- Right-click the Security log and select Filter Current Log.
- In the Filter Current Log dialog, enter the relevant Event IDs for logon and logoff events, such as 4624 for successful logons and 4634 for logoffs.
- Click OK to apply the filter and view only the filtered events.
4. Analyzing the Event Details: Reviewing the details of each event helps in understanding the context and implications of the logon or logoff activity. Here are the steps:
- Double-click an event to open its details.
- Examine information such as the user account, logon type, timestamp, and machine name to understand the activity.
Using PowerShell
1. Running PowerShell Commands: PowerShell provides a powerful way to query and retrieve login and logoff data through scripting. Here are the steps:
- Open PowerShell with administrative privileges.
- Use commands like Get-EventLog or Get-WinEvent to query the security logs.
2. Retrieving Logon Data: Execute PowerShell commands to extract logon events. Here’s the example command that retrieves all successful logon events (Event ID 4624) and displays the time and message:
- Get-WinEvent -FilterHashtable @{LogName=’Security’; Id=4624} | Format-Table TimeCreated, Message -AutoSize
3. Retrieving Logoff Data: Use similar commands to extract logoff events. Here’s the example command that retrieves all logoff events (Event ID 4634) and displays relevant details:
- Get-WinEvent -FilterHashtable @{LogName=’Security’; Id=4634} | Format-Table TimeCreated, Message -AutoSize
4. Customizing PowerShell Scripts: Customize scripts to generate detailed reports or automate data extraction. The script exports logon events to a CSV file for further analysis:
- $logonEvents = Get-WinEvent -FilterHashtable @{LogName=’Security’; Id=4624}
- $logonEvents | Export-Csv -Path “C:\LogonEvents.csv” -NoTypeInformation
Analyzing and Interpreting Login/Logoff data
Once you can view Active Directory login and logoff data, the next step is to analyze and interpret this information to derive actionable insights. Effective analysis can help you detect anomalies, and improve overall security. Here’s how to approach this task:
Identifying Suspicious Activity
To ensure the security of your AD environment, start by looking for unusual or suspicious activities in the login history. Key indicators of suspicious activity might include:
- Unusual Login Times: Logins occurring at odd hours or outside regular working hours can be a sign of unauthorized access.
- Frequent Failed Logins: A high number of failed login attempts may indicate a brute force attack or unauthorized access attempts.
- Login from Unexpected Locations: Logins from unfamiliar or unexpected IP addresses or locations could signal a potential security breach.
Understanding Patterns and Trends
Analyzing login data helps in recognizing patterns and trends that can be indicative of potential issues or security threats:
- Normal vs. Abnormal Patterns: Establish baseline login patterns for users and detect deviations. For example, if a user normally logs in from a single location and suddenly logs in from multiple geographic locations, this could be a red flag.
- Trend Analysis: Look for trends over time, such as increased login attempts, which may indicate rising security risks or issues that need addressing.
- User Behavior: Understanding typical user behavior can help in identifying anomalies. For example, if a user’s login activity suddenly increases or changes significantly, it might warrant further investigation.
Reporting and Documentation
Accurate reporting and documentation are vital for tracking security issues and ensuring compliance:
- Regular Reports: Generate and review regular reports on login activities to keep track of any unusual patterns or incidents. This helps in maintaining an ongoing overview of user activity.
- Incident Documentation: Document any suspicious activities or security incidents thoroughly. Include details such as the nature of the suspicious activity, affected users, and actions taken.
- Compliance: Ensure that your reporting aligns with organizational policies and compliance requirements, maintaining detailed logs for audits and regulatory purposes.
Leveraging Third-Party Tools
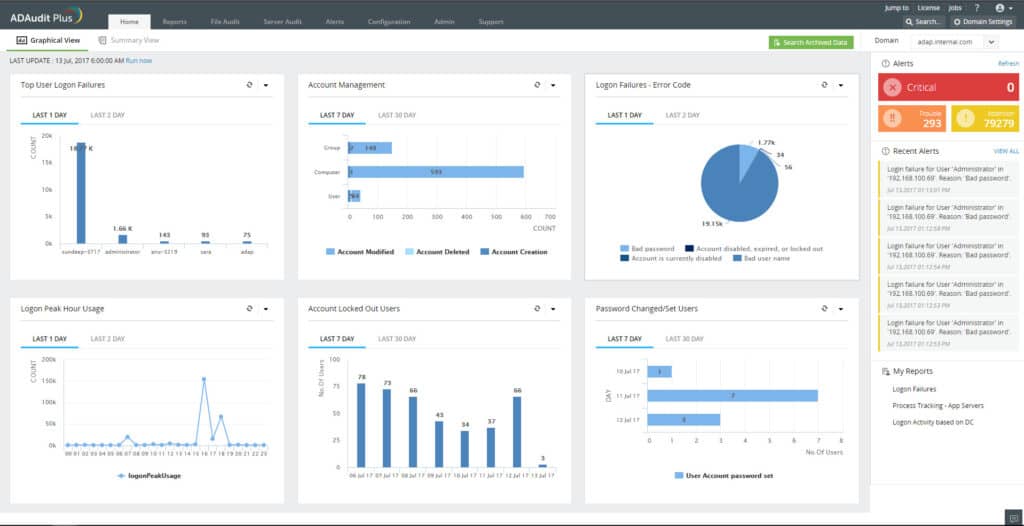
ManageEngine ADAudit Plus – FREE TRIAL
Third-party tools like ManageEngine ADAudit Plus can significantly streamline the process of analyzing and interpreting AD user login history. Here’s how:
- Automated Monitoring: ManageEngine ADAudit Plus provides automated monitoring of user login activities, making it easier to spot suspicious behavior in real time.
- Advanced Reporting: It offers advanced reporting features that can generate detailed, customizable reports on login activities, failed login attempts, and more.
- Trend Analysis: The tool helps in identifying trends and patterns through comprehensive dashboards and analytics, allowing for proactive security measures.
- Alerting and Notifications: It includes alerting mechanisms that notify administrators of unusual activities or policy violations, facilitating quicker responses to potential security threats.
While ADAudit Plus is a great example, there are many other effective third-party tools with diverse features and functionalities that can do the same job. It’s therefore important to assess your specific needs and budget before making a decision. Start by registering for a 30-day free trial.
Conclusion
The process of viewing and auditing AD user login history involves not only collecting and configuring the necessary data but also analyzing and interpreting it to safeguard against potential security threats. By following the outlined steps, you can ensure that your AD environment remains secure, compliant, and well-managed.
As technology and security landscapes evolve, the methods and tools for Active Directory auditing will also change. Keeping up with the latest advancements in auditing tools, techniques, and best practices will help you adapt to new challenges and maintain an effective auditing strategy.