Our smart devices and the applications installed on them act as an extension of ourselves. However, each of these poses a potential risk when connected to the internet. Each application and device acts as an attack surface that can provide intruders with a doorway into our networks and media. Attack surface monitoring plays a vital role in mitigating such possibilities of exposure and aims to eliminate any opportunities for compromise.
Here is our list of the best attack surface monitoring tools:
- Intruder – EDITOR’S CHOICE This website-based external attack monitoring service also offers network vulnerability scanning and dynamic application security testing options. Access a 14-day free trial.
- ManageEngine Vulnerability Manager Plus – FREE TRIAL A software tool that assists businesses and organizations in identifying, evaluating, and fixing security vulnerabilities in their networks and systems. Get a 30-day free trial.
- ManageEngine ADAudit Plus – FREE TRIAL A comprehensive security tool that continuously audits your security posture to identify misconfigurations, identity risks, and other AD attacks. Start a 30-day free trial.
- Bugcrowd Attack Surface Management Offers one of the most advanced attack surface monitoring tools and services available in the market.
- Reliaquest GreyMatter A rather different from the average attack monitoring tool that focuses on the system under review and tries to identify places for improvements within the application.
- CoalFire Attack Surface Management The security measures of third-party software are always questionable. This calls for a service like CoalFire to identify the scope of the attack surface and then appropriately assess the risks.
- Burp Suite Primarily focuses on software development companies that are developing and managing multiple applications and websites.
- Zed Attack Proxy An open-source program frequently used by security experts around the world to identify their system’s vulnerabilities and make necessary improvements accordingly.
- ImmuniWeb The most comprehensive attack surface monitoring and vulnerability identification tool on our list.
- CyCognito A well-reputed attack surface monitoring tool utilized by brands around the world to help safeguard their systems.
But what is Attack Surface Monitoring?
Every software when developed has certain entry points i.e.: loose ends, placed both advertently and inadvertently, that can be used to gain unauthorized or backdoor access (depending upon your intentions) to the application’s database and manipulate it according to your intentions. These entry points are referred to as ‘attack surface’ and can both be a menace as well as a blessing in disguise to gain access to a system.
Attack surface monitoring involves an active review and analysis of programs to identify such possible points of entry so that they can be appropriately addressed to make the program as secure and air-tight as possible. It can actively reduce the possible risks that an application of the modern-day may face and provides developers with opportunities for optimization with improved code.
What compromises the Attack Surface?
Attack surface might feel like a software-related term that has something to do with the lines of code which comprise the application. Attack surfaces are much broader than what one might generally think.
An attacks surface comprises of the following three components:
- Physical Attack Surface The physical attack surface includes all potential points of entry that can be physically accessed to enter into a system or a network. These include computers connected with the system, servers, laptops, modems, access points, routers, printers, and even security cameras that can serve as the most convenient physical attack surface. These when coupled with a sold-out employee can make a destructive combo that has the potential for a disaster any time of the day.
- Social Attack Surface Humans are social beings; they cannot help but interact with hundreds of people daily without even realizing they have done so. In addition to this, the human mind is not programmed like some lines of code that devise a certain line of action in a certain circumstance. The way it functions is a wonder in itself but it can be tricked into performing actions that might not opt had it been more aware of the situation. Employees at organizations can get stalked in public places and may end up casually leaving a loose end for a potential breach e.g.: a person watching over your shoulder can see your password as you type it to log in to your laptop and see an update about an upcoming meeting during your coffee at Starbucks. It demands vigilance and skepticism to be on your toes at all times so you do not end up letting any make a fool of you.
- Digital Attack Surface As our original expectation was, the digital attack surface is indeed the opportunity embedded within the software that can be a possible point of intrusion. These include virtual points of intrusion that can be used to break into the system. Digital attack surfaces include servers, websites, databases, applications, cloud networks, and even operating systems.
How To Reduce Your Attack Surface
If you are thinking, ‘all of this is quite messed up, what should I do’, then we share the same thoughts. Here are some tips and tricks that might come in handy and save you from trouble. Of course, the inherent nature of software is such that it is impossible to eliminate all risks, but you can follow a few best practices.
To avoid intrusion from a physical attack surface:
- Establish access controls over different levels of hardware concerning their vulnerability e.g.: a person from the billings and finance department does not access the server room. Similarly, a newly hired IT assistant should not be allowed unmonitored access right away. This is not to say that people are dishonest. This is just another ‘better safe than sorry’ measure.
- Advise employees and users systems to be aware of their surroundings and to opt for practices that are safe and steer them away from trouble e.g.: leaving your passwords on a sticky note at your desk is just carelessness, avoid it at all costs.
The reality that a social attack surface exists means you have to be cautious:
- It is best if you can avoid using your laptop computers in the public but when you do not have a choice, try to use them in a place with minimum activity. Try to be in a position where no one can look over your shoulder (you ever who is stalking you, when and where) and NEVER leave your device unlocked and unattended.
- Social interactions are part of what makes us human. Beware that some person you met at the party who seems to be more interested in your job than you, could be a criminal mind who is after your and your company’s money and not a potential candidate for your future friend.
Physical and social attack surfaces are inherently risky but they can seldom result in a big problem without the digital attack surface. In the end, it is the systems and the databases that the devious minds are after. Digital attack surfaces although require greater intricacies for protection, some measures do belong to everyday usage and should at all levels:
- Do not plug-in unknown devices into your laptop or computer especially if it is a USB stick or a memory card you found by the doormat.
- Be careful with your online activity, there are phishing links and devious sites scattered all over the internet. No matter how enticing the offer is, if you are not sure about the website’s safety, stay away.
- VPN services are available for prices as low as $2.49 a month and support even more than 5 devices at a time. Something even this cheap can add layers of protection between you and a potential risk so why not invest in time and save yourself from the hassles.
- Get your systems reviewed for attack surfaces periodically from ethical hackers and digital security experts. They can then devise security patches for your software and make it safer for usage in the future.
Now all of this might seem intimidating, scary, and try to shatter one’s trust in humanity but it is quite the contrary. Some of these measures might feel too trivial to even care about but it is the collective effort to follow these practices that will guarantee better security for all individuals in the ecosystem and the entire internet at a broader scale.
Advanced Attack Surface Monitoring
The field of cybersecurity is a continuously evolving field of study where things change as quickly as drinking a cup of coffee. It is not just that you need to have all fronts covered and have strategies in place that you have learned from past battlefields but also stay one step ahead of the malicious mind who might try to take advantage of you.
This demands all the help and skill that you can acquire to secure your fort from all fronts. Do not just bar the gates, have soldiers at the windows and another set of soldiers in the hallways to contain the intrusion in case of a misfortune happening.
Attack surface monitoring tools can be a great help in this matter. They are specially developed by individuals who are well-aware of the latest tactics in the market being used by hackers to fulfill their evil desires.
A good attack monitoring tool has the following characteristics:
- Maintains a detailed log of the requests made for data access
- Track and notify in case of any suspicious activity or unusual volume of requests
- Scan the software for vulnerable points for improvements
- Identify potential risks for data loss and devise measures to minimize it
- Offer a sufficient trial period to test it for a well-informed decision
The Best Attack Surface Monitoring Tools
Our methodology for selecting attack surface monitoring tools and software
We reviewed attack surface monitoring tools and analyzed the options based on the following criteria:
- Ability to continuously monitor various attack surfaces
- Support for advanced monitoring and reporting
- Support for enterprise environments
- Integrations into other SIEMs and security platforms
- Graphical interpretation of data, such as charts and graphs
- A free trial period, a demo, or a money-back guarantee for no-risk assessment
- A good price that reflects value for money when compared to the functions offered
Here are our shortlisted attack surface monitoring tools that promise to provide the best digital attack surface risk mitigation that exists out there.
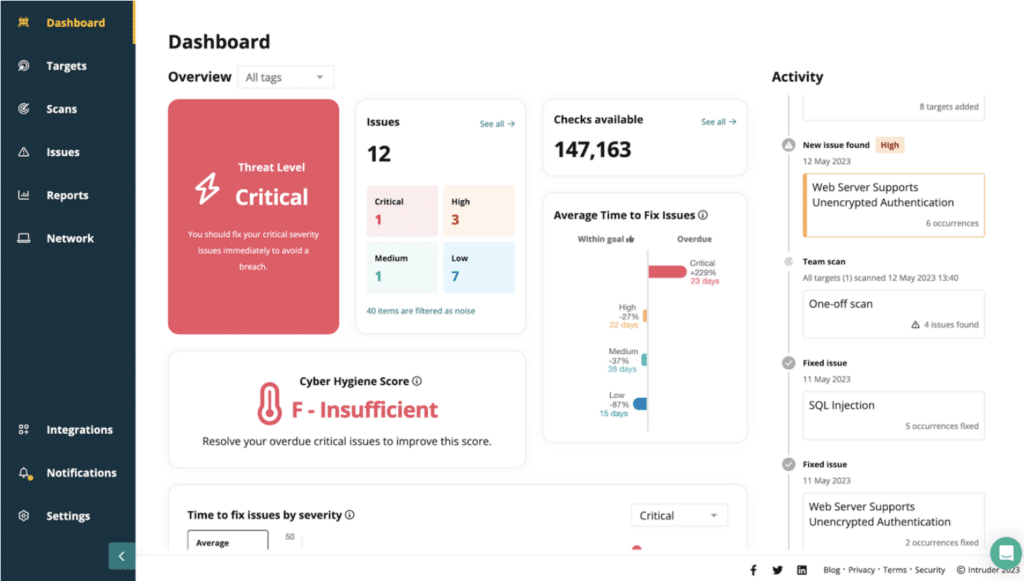
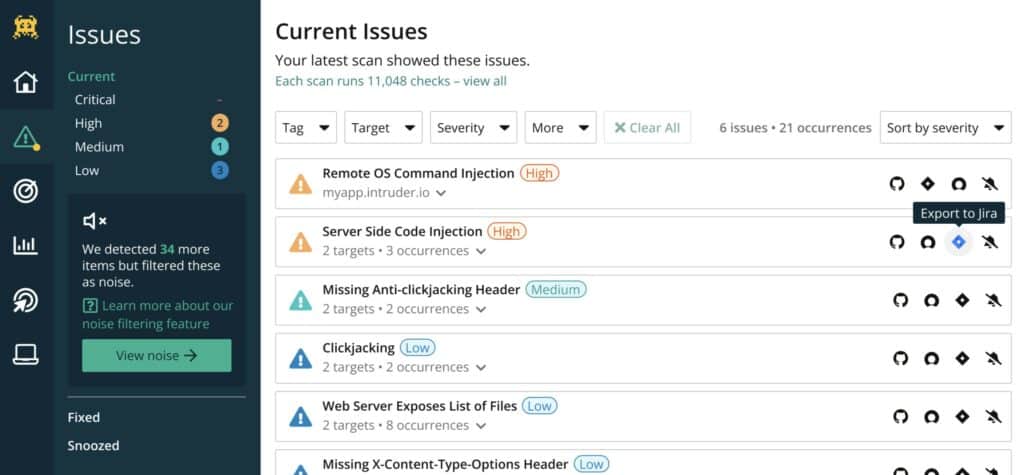
1. Intruder – FREE TRIAL
Intruder is a hosted version of the OpenVAS vulnerability scanner and the platform also offers a hosted Tenable service. Both of these options provide attack surface monitoring and the Tenable service also provides network vulnerability scanning.
Key Features:
- Hosted OpenVAS
- Tenable option
- Attack surface testing
- Internal scanning
- On-demand vulnerability scans
Why do we recommend it?
Intruder.io is a web-based vulnerability scanner that offers three levels of service and all of them include attack surface scanning. The frequency of scans that you get from the service depends on which plan you opt for. You can also get on-demand scanning that you can launch yourself.
With the Essential plan, you get a monthly external scan with unlimited on-demand scans, which are ideal for compliance. The Pro edition gives you unlimited scheduled external and network scans, which can also be run on demand and plenty of integrations to simplify your workflow. Premium adds the services of a rapid response team to the Pro plan.
You can set this attack surface scanner to run as often as you like and it also provides internal vulnerability scanning. You need to install agents on your endpoints to get that internal system to run. Intruder also provides dynamic application security testing (DAST) for Web applications and APIs that can be set up as a continuous tester for a CI/CD pipeline.
Who is it recommended for?
This is an interesting service for businesses that don’t have cybersecurity experts on the payroll. This is because the tool provides OpenVAS or Tenable, depending on which plan you choose, which you could get directly but you would need to know how to use them. The Intruder simplifies and automates the management of those vulnerability scanners.
Pros:
- Attack surface monitoring for all budgets
- Options for on-demand vulnerability scanning
- Integrations with project management tools
- Data exchanges with team collaboration systems
Cons:
- More features can be unlocked on the higher plans
This attack surface scanner service is available on the Intruder website and is very easy to set up. Assess the tool with a 14-day free trial.
EDITOR'S CHOICE
Intruder is our top pick for an attack surface monitoring tool because it offers an easy way to assess your entire system for external vulnerabilities that you launch from a website. The service offers OpenVAS or Tenable and it makes system protection affordable for small businesses while also offering a top-of-the-line service for companies with bigger budgets. This system also gives you options for internal vulnerability scanning and it has a DAST add-on for scanning Web applications and APIs.
Download: Access the 14-day FREE Trial
Official Site: https://portal.intruder.io/free_trial
OS: Cloud-based
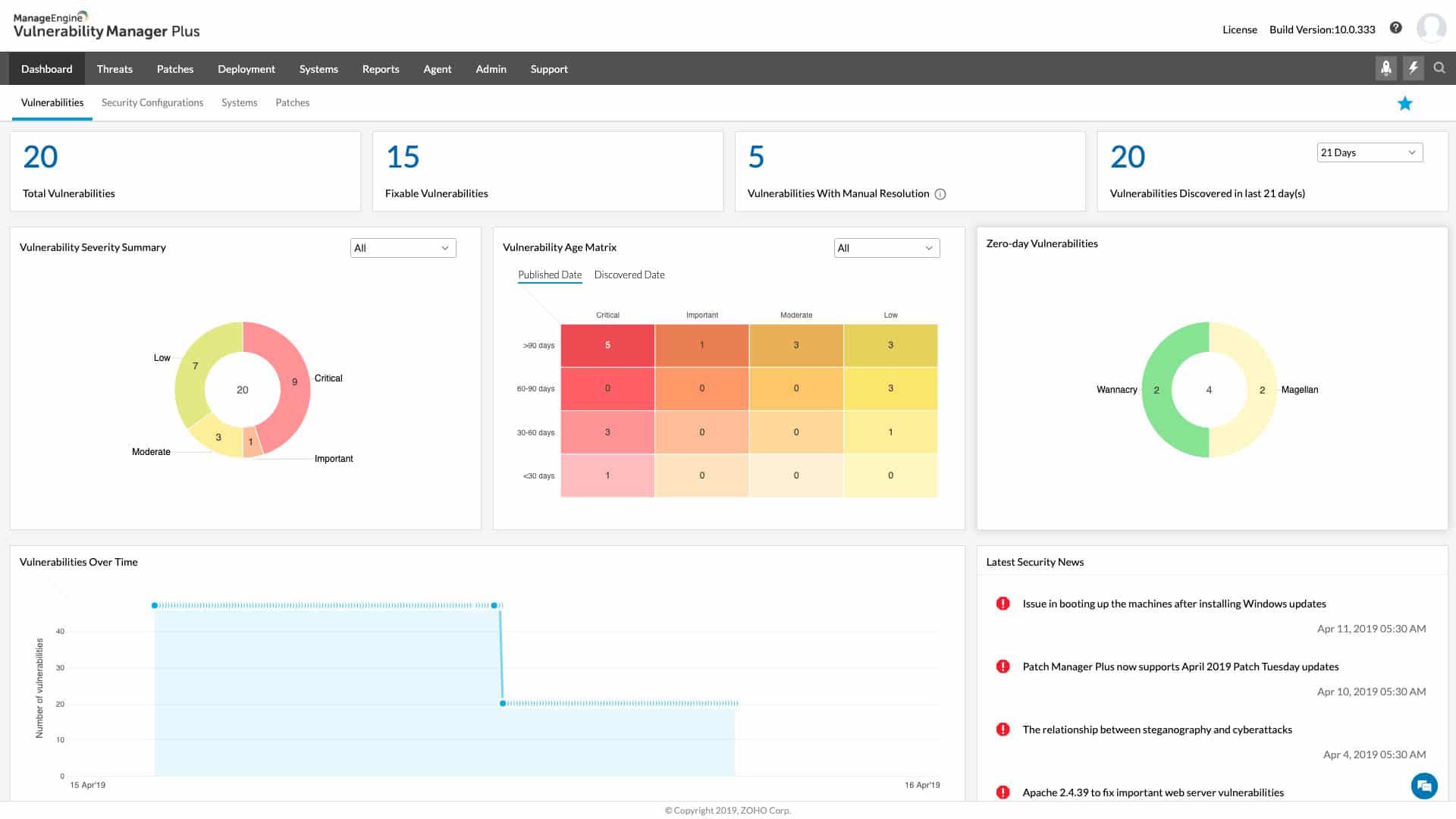
2. ManageEngine Vulnerability Manager Plus – FREE TRIAL
ManageEngine Vulnerability Manager Plus offers a variety of tools and features for vulnerability assessment and management, including vulnerability scanning, risk assessment, reporting, and more.
Key Features
- Automated management of drivers
- Customized recovery methods using templates
- Easy management of user profiles
Why do we recommend it?
ManageEngine Vulnerability Manager Plus works within the network and, in fact, focuses on endpoints. The tool looks for configuration errors that could provide inroads for hacks and produces a list of tasks to fix any discovered problems. The package also includes a patch manager that updates out-of-date software.
Using Vulnerability Manager Plus, users can scan their networks and systems for vulnerabilities, determine the risks associated with them, and create plans to address them, thereby improving their overall security posture and reducing the likelihood of cyber attacks. Vulnerability Manager Plus also includes regularly scanning for vulnerabilities, generating reports and alerts, and prioritizing vulnerabilities based on risk levels.
Who is it recommended for?
This service can scan computers running Windows, macOS, or Linux. There are three editions of the package, which makes it suitable for all sizes of businesses. The Free edition, for small businesses, will cover up to 25 endpoints. The two paid editions are Professional, for LANs, and Enterprise, that covers multiple sites.
Pros:
- Provides intuitive imaging and deployment while allowing for technical customization
- Offers flexible pricing options for both small businesses and enterprises
- Suitable for use in multi-site organizations with remote office deployment capability
- Can deploy images on any hardware
Cons:
- Primarily designed for sysadmins, so non-technical users may need to spend time learning how to use the application.
ManageEngine Vulnerability Manager Plus offers a free 30-day trial.
3. ManageEngine ADAudit Plus – FREE TRIAL
ManageEngine ADAudit Plus is an attack surface analyzer that collects data from multiple devices on your network to analyze and correlate them for insights. Specifically, it looks for Indicators of Compromise (IoC) that can help detect 25+ attacks. It also identifies network and process-level events, risky user behavior, and other Indicators of Exposure (IoE) that could signal potential issues.
Key Features:
- Leverages machine learning to find anomalous events.
- Automates responses to specific incidents.
- Backs up all AD objects and restores them when needed.
- Spots security misconfigurations.
- Generates a wide range of reports.
Why do we recommend it?
We recommend ManageEngine ADAudit Plus because it continuously monitors your attack surfaces to identify any potential vulnerabilities. It also covers many types of vulnerabilities, like misconfigurations, identity risks, AD-related attacks, risky user behavior, process and network-level attacks, lateral movement attacks, and more. With such broad coverage, you can stay one step ahead of your security at all times.
One of the aspects we love about this tool is its correlation. Besides taking log data from all the devices in your network, it also takes in threat intelligence feeds to provide in-depth insights. Its focus on Indicators of Compromise (IoC) and Indicators of Exposure (IoE) makes it well-suited for thwarting most attacks.
Moreover, it generates reports that help with forensic analysis, compliance, and auditing.
Who is it recommended for?
It is recommended for newtok engineers and security teams of organizations of all sizes. It can also come in handy for MSPs who oversee the security of client organizations.
Pros:
- Covers most well-known vulnerabilities.
- Integrates well with popular tools, AD environment, and the ManageEngine ecosystem.
- Generates reports for better visibility.
- Automates incident response to save time and effort.
Cons:
- Initial setup may require technical expertise.
ADAudit Plus starts at $595 per year. Download a 30-day free trial to get started.
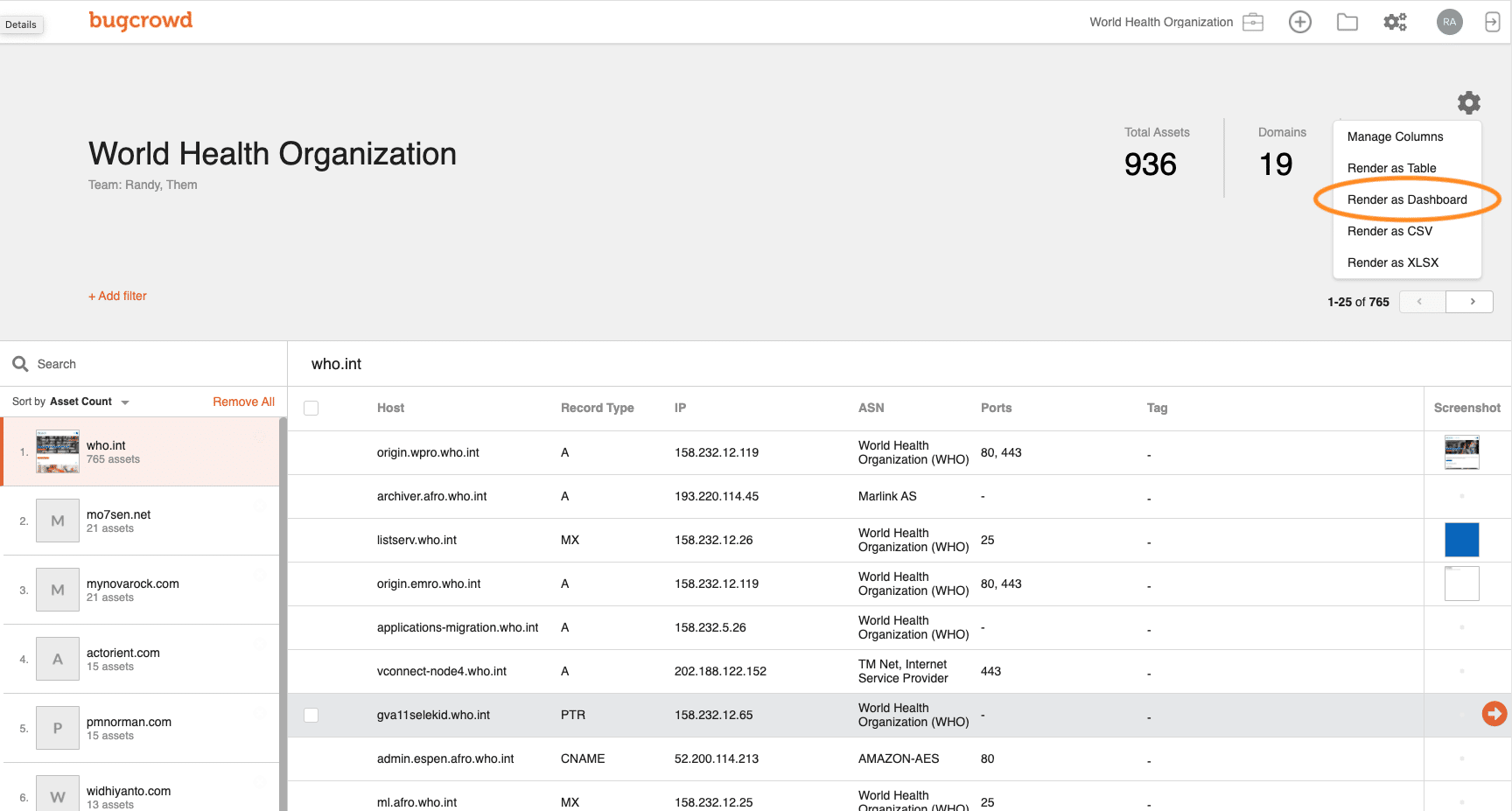
4. Bugcrowd Attack Surface Management
Bugcrowd Attack Surface Management offers one the most advanced attack surface monitoring tools and services available in the market. A very enticing offer from the company includes an automated crawler that integrates itself with the system and crawls through its dimensions in all directions to identify lacunas that can be used by attack vectors to penetrate the system.
Key Features:
- Operates a bug bounty
- External attack surface scanning
- Endpoint and device scanning
Why do we recommend it?
Bugcrowd Attack Surface Management scans your system for possible access points that hackers would discover. This is a system that was created by penetration testers, who are white hat hackers. The company maintains a large database of discovered security weaknesses and checks your system against that list.
Their offerings are not just limited to software-based services. Bugcrowd has a handful of well-trained ethical hackers also referred to as ‘white hat hackers that try to penetrate the application under review via different methods and thus, identify loopholes in this way.
All services are primarily cloud-based and can be utilized remotely so you do not have to compromise on your system’s security just because you can not reach out to these people. The company even offers a trial so you can decide for yourself whether you want to continue with their service or not after you have a taste of their treat.
Who is it recommended for?
Bugcrowd pays a bug bounty to anyone who discovers a security weakness in any hardware or software system. This enables it to gather a very long list of hacker tips and it uses that against your system. This is an automated service but you can also hire the company to put a human team of penetration testers to work on discovering weaknesses in your system.
Pros:
- Has a private list of discovered vulnerabilities that other security services don’t know about
- Tests all clients when a new vulnerability is discovered
- Human penetration testing option
Cons:
- Could be too expensive for small businesses
5. Reliaquest GreyMatter
Reliaquest GreyMatter is rather different from our average attack monitoring tool. While other attack surface monitoring tools focus on the system under review and try to identify places for improvements within the application, GreyMatter keeps an eye out for you on the dark web for any intel should someone be considering to attack your system.
Key Features:
- Dark Web scanning
- Data breach detection
- Identifies compromised accounts
Why do we recommend it?
Reliaquest GreyMatter extends attack surface management out to the world by scanning the Dark Web for mentions of corporate assets, such as account credentials or email addresses and also information on impending attack campaigns for specific industries or corporate groups. The scanner implements both internal and external attack surfaces and triggers automated defenses.
Think of GreyMatter as your intelligence service that crawls through the dark web and looks for any information that can result in a security breach to your system. The crawler notifies the system about any circulating information on the dark web as well as strategies that have been used against victim companies in the past. This way you can get yourself geared up well in time to prevent a misfortune incident.
Who is it recommended for?
This is an extensive package and it is able to integrate into your existing security systems. This means that it will extract data from your access rights manager, firewalls, and SIEM. The integration process is a little complicated and would require experienced security experts. So, this is a solution for large companies that already have cybersecurity staff on the payroll.
Pros:
- Intelligence gathering on the Dark Web
- Spots chatter on hacker sites that could lead to an attack
- Can identify insider threats
Cons:
- Results are difficult to assess – there might never be an attack planned against your business
You can assess the GreyMatter platform by accessing a demo.
6. CoalFire Attack Surface Management
CoalFire Attack Surface Management is a combination service that includes automated Dark Web scans with manual penetration testing. If you sign up to the service, CoalFire adds your business’s identities to its database. These include company brands, product names, domains, and addresses. The threat intelligence crawler will then look specifically for mentions of your company, user accounts, or email addresses for signs of data leaks or attack planning.
Key Features:
- Offensive security
- Network security monitoring
- Application security
Why do we recommend it?
CoalFire Attack Surface Management is an impressive combination of both automated systems and consultancy services. The threat intelligence gathered by the package is tailored to the customer and includes threats that might be targeting an industry or even a location as well as those threats that directly aim for the company.
Alongside its Dark Web scanning, CoalFire Surface Management provides vulnerability scans for clients. That’s an automated process and will reveal common security weaknesses. The company also offers the services of a penetration testing team to really probe a system in the way that a hacker would.
Who is it recommended for?
Penetration testing services are expensive. They are at the top end of the attack surface monitoring market because they provide the services of highly paid cybersecurity experts. Automated vulnerability scanners are a lot cheaper. So, this offer will be out of the reach of small businesses.
Pros:
- A combination of automated testing and manual penetration testing
- Tests networks, servers, applications, cloud platforms, and IoT devices
- A tailored service for each customer
Cons:
- No free trial
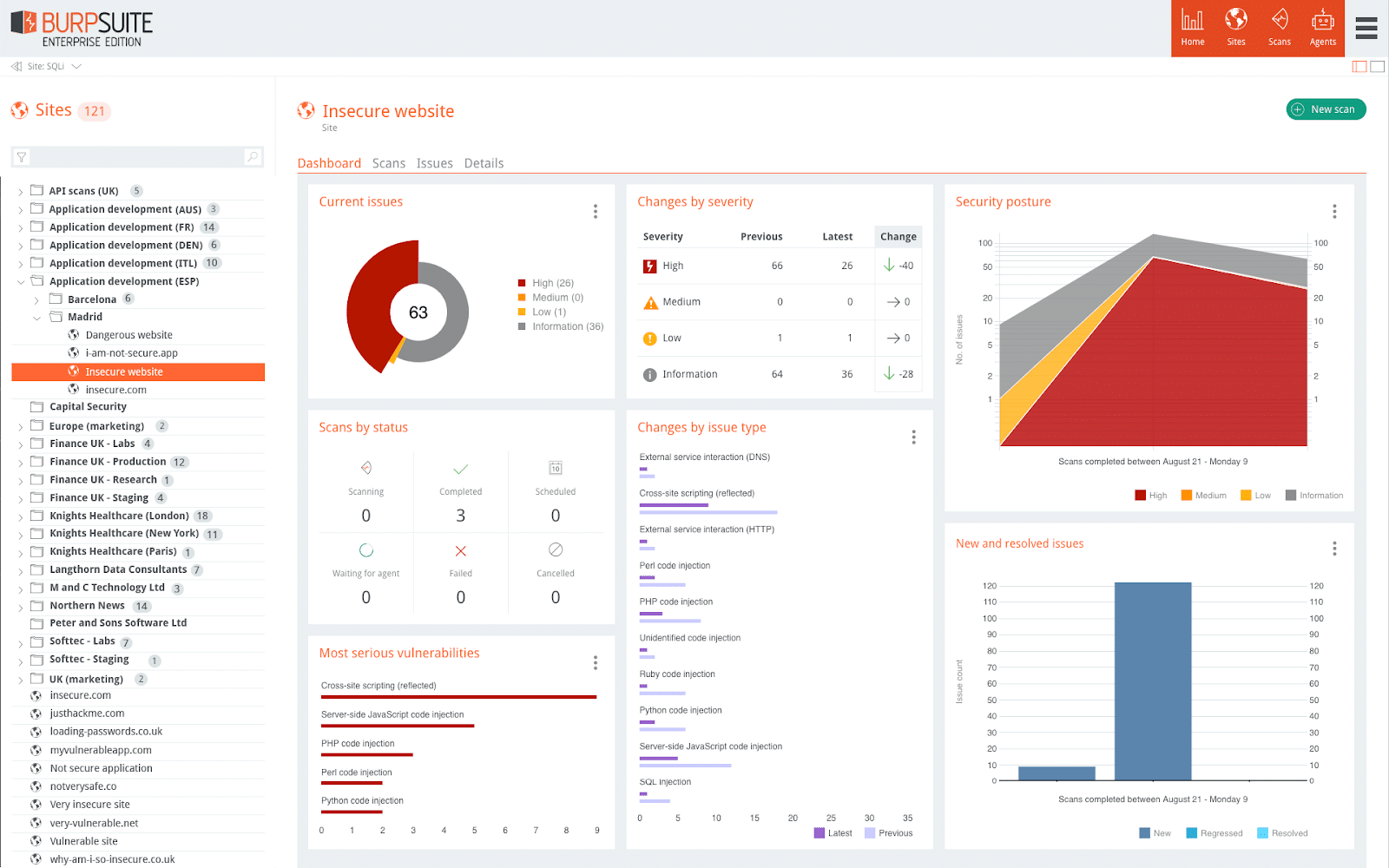
7. Burp Suite
Burp Suite is a penetration testing framework and also has vulnerability scanning capabilities. The way you use Burp Suite greatly depends on the edition that you purchase. The Community Edition of Burp Suite is the source of its acclaim. This is a free tool for use by penetration testers. Its use forms part of every cybersecurity course.
Key Features:
- Free and paid versions
- Penetration testing tools
- Vulnerability scanner
Why do we recommend it?
Burp Suite offers a framework for manual penetration testing and a vulnerability scanner. The tool also has a version for Web application security testing. The penetration testing utilities in the package include both reconnaissance and attack tools. While there is a degree of automation on the Community Edition, this is in the form of a series of tests that work through combinations of input values.
Penetration testers would use the Community Edition. The Professional Edition provides all the penetration testing tools plus an automated vulnerability scanner. The Enterprise edition is specifically designed for scanning Web applications. That top plan used to include a facility for security testing in CI/CD pipelines. However, that function for development teams has now been moved into a separate tool called Dastardly.
Who is it recommended for?
The Community Edition is designed for use by penetration testers. Hackers usually only use free tools and the penetration testing sector follows suit, so the paid editions won’t appeal to that audience. The two paid editions are designed for use by consultancies and they could be used by large companies. However, they are expensive and wouldn’t appeal to small businesses.
Pros:
- Free penetration testing tools
- Paid vulnerability scanner
- This system operates as a proxy to probe Web vulnerabilities
Cons:
- The paid edition could be too expensive for small businesses
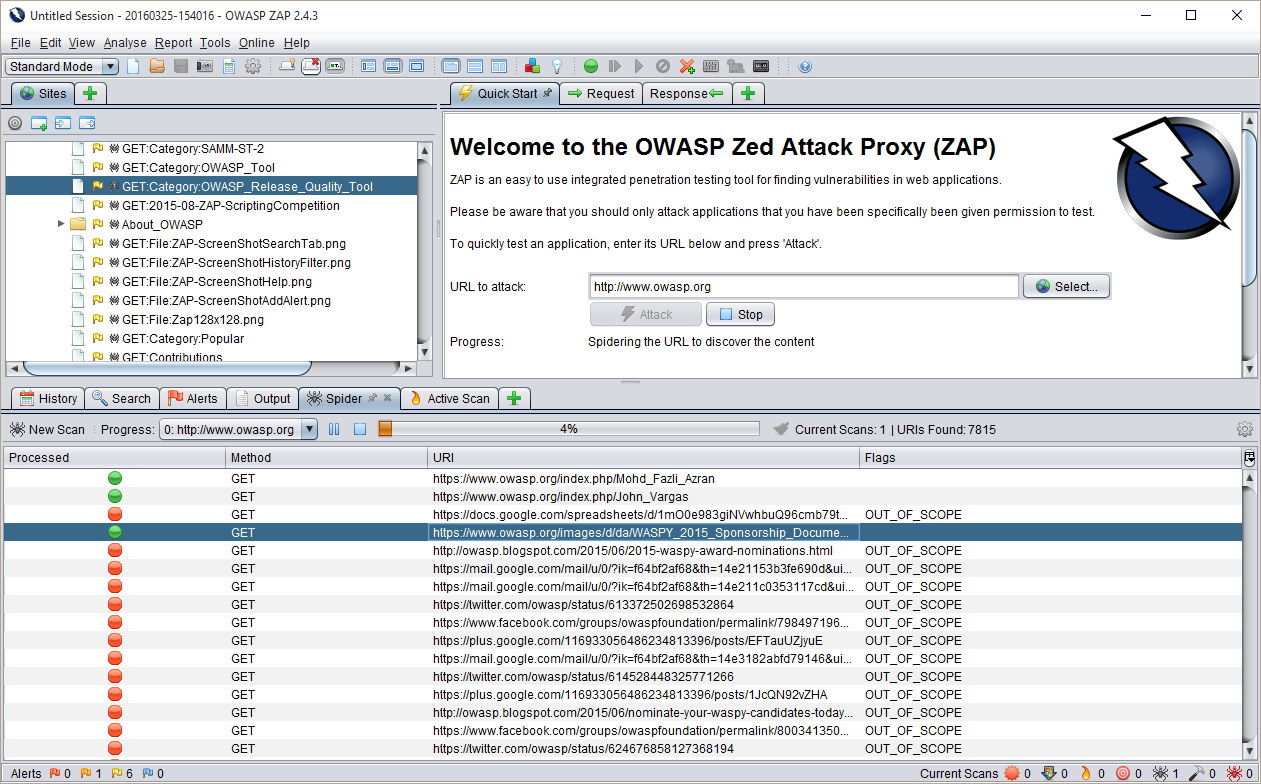
8. Zed Attack Proxy
The Zed Attack Proxy, better known as ZAP, was until recently a project of the Open Web Application Security Project. It has now moved to be the responsibility of the Linux Foundation. However, it is still an open source system and it is still free to use. This tool sites between your web server and a browser, intercepting the traffic that assembles a web page and it scans that code for vulnerabilities.
Key Features:
- Web proxy
- Extensible
- Free to use
Why do we recommend it?
ZAP is a highly respected penetration testing tool. The package scans web page code for weaknesses, such as cross-site scripting, cross-site request forgery, and SQL injection possibilities. This system needs to be installed on a computer that is between the web server and the testing browser but it can be on the same computer as the browser.
As it is an open source system, the code is frequently tested and enhanced by volunteer developers. These enthusiasts also create plug-ins for the system that extend its capabilities to scan specific technologies without altering the core code. There is a large library of these plug-ins and getting to know them all and how to integrate them into the program makes this tool difficult to use.
The Zed Attack Proxy is a software package that will install on Windows, macOS, and Linux. You can download ZAP for free from the project’s website.
Who is it recommended for?
This is a tool for use by penetration testers. You need to spend time to get to know how to use the tool effectively, and once you have acquired that knowledge, you have a marketable skill that would be put to more efficient use as a consultant than as an IT department technician. Infrequent use can mean you have to relearn the tool every time.
Pros:
- Attacks are implemented by activating a free plug-in
- Can be used for intelligence gathering
- Includes a scripting language
Cons:
- This is not an automated monitoring system but a penetration tool
9. ImmuniWeb
ImmuniWeb is the most comprehensive attack surface monitoring and vulnerability identification tool on our list. ImmuniWeb offers multiple services enveloped inside one comprehensive package. The company offers tools that integrate with your system to identify ‘weak moments’ and advise on how to free the security dam of any leaks.
Key Features:
- Vulnerability scanning
- Dark Web scanning
- Free and paid versions
Why do we recommend it?
ImmuniWeb is a large platform of penetration testing tools and vulnerability scanners. The system can test the security of networks, web assets, APIs, cloud platforms, and endpoints. The package also includes Dark Web scanning and threat intelligence. The paid system is supplemented by a library of free tools – you don’t have to be a subscriber to use those Community Edition utilities.
Not only this, but it also looks out for you and your company for any news on the dark web and warns in case it senses any activity that can lead to a data breach. The combination of the two services is what any company can wish for. Additionally, the optimized communication between the internal and external crawlers enables ImmuniWeb Discovery to analyze the system from both ends and helps tie up loose ends well in time.
The company offers 4 different plans; Express Pro, Corporate, Corporate Pro, and the fully-stacked Ultimate. You may find the prices quite heavy on the pocket but that is the price you must pay if you host a high-risk database and cannot dare to compromise on the system’s security by even the slightest extent. ImmuniWeb will make sure you get your annual targets for data security right.
Who is it recommended for?
Companies and consultancies would use the paid ImmuniWeb AI platform. The Dark Web scanner has to be given the details of a specific company in order to be effective. Smaller companies that want to assure their security can access the free tools of the Community Edition and these would also be of use to penetration testers and security consultancies.
Pros:
- The paid version uses AI to identify weaknesses in a series of assets
- Includes security testing for mobile apps, Web apps, on-site assets, and IoT devices
- Provides phishing campaigns to test user security awareness
Cons:
- This is a very large package of tools and any business would need a security expert on staff to run it
10. CyCognito
CyCognito is a well-reputed attack surface monitoring tool utilized by brands around the world to help safeguard their systems. CyCognito primarily focuses on publicly exposed assets that serve as your online face to the world, pick out the lice in these assets and help you mitigate the risk by tightening up your security measures.
Key Features:
- Automated Discovery
- Active Security Testing
- Risk Prioritization
Why do we recommend it?
The CyCognito platform includes a number of tools for preventative cybersecurity protection. Its Attack Surface Management unit is a Dark Web scanner. It documents all of the identities that your company shows to the outside world, such as email addresses, domains, and brands, and then searches for that information on the Dark Web.
You can choose to combine attack surface monitoring with CyCognito with other services such as vulnerability management for a more thorough check on your system.
Who is it recommended for?
Dark Web scanning is something that no company can set up by itself. You need to contract in a specialist service, such as CyCognito to get a proper exposure assessment. The CyCognito platform also includes a vulnerability scanner, which looks for attack opportunities.
Pros:
- Uses machine learning (ML), natural language processing (NLP), and graph data modeling to autonomously discover assets across the enterprise, including cloud environments
- Provides detailed context about assets, including ownership, business purpose, attractiveness to attackers, and related assets
- Offers detailed supporting evidence, asset ownership information, and actionable validation guidance to streamline remediation efforts
Cons:
- No free trial
In short
Attack surface monitoring is a crucial part of keeping any website, application, and organization secure and safe from any undesirable consequences. With everything from classrooms to currencies turning digital, we must stay aware and vigilant for any malicious intents and keep our troops ready when someone tries to bring down our fort.
Attack Surface Monitoring Tools FAQs
How often should an organization perform attack surface monitoring?
The frequency of attack surface monitoring depends on the size and complexity of the organization's network and systems, as well as the level of risk associated with its operations. In general, regular monitoring is recommended to proactively identify and address potential vulnerabilities.
How can attack surface monitoring help with incident response?
Attack surface monitoring can help with incident response by providing real-time alerts and notifications when potential vulnerabilities or security incidents are detected, enabling IT teams to quickly respond and mitigate the issue.
What are some best practices for attack surface monitoring?
Best practices for attack surface monitoring include regular vulnerability assessments, penetration testing, web application scanning, and ongoing employee training and awareness.
What types of organizations can benefit from attack surface monitoring?
Organizations of all sizes and industries can benefit from attack surface monitoring, particularly those with large or complex networks, high-value assets, or regulatory compliance requirements.
How can attack surface monitoring be integrated with other security tools?
Attack surface monitoring can be integrated with other security tools, such as SIEM (Security Information and Event Management) and threat intelligence platforms, to provide a more comprehensive view of an organization's security posture and potential vulnerabilities.
What are some common challenges associated with attack surface monitoring?
Common challenges associated with attack surface monitoring include the complexity of modern IT environments, the sheer volume of potential vulnerabilities, and the need for specialized technical skills.
How can machine learning and artificial intelligence be used for attack surface monitoring?
Machine learning and artificial intelligence can be used for attack surface monitoring to automate the detection of potential vulnerabilities and security threats, and provide real-time alerts and recommendations for remediation.
How can attack surface monitoring help with risk management?
Attack surface monitoring can help with risk management by identifying and prioritizing potential vulnerabilities based on their level of risk and impact on the organization's operations.