Cloud Security Posture Management (CSPM) automates the detection and remediation of threats in cloud infrastructures such as Infrastructure as a Service (IaaS), Software as a Service (SaaS), and Platform as a Service (PaaS). CSPM can apply best practices for cloud security across hybrid, multi-cloud, and container systems universally, and can be used for risk visualization and assessment, incident response, compliance monitoring, and DevOps integration.
Importance of CSPM
A cloud may join and disconnect with hundreds or even thousands of other networks throughout a day. Clouds are powerful because of their dynamic nature, but they are also difficult to protect. The difficulty of safeguarding cloud-based systems gets increasingly significant as a cloud-first attitude becomes the norm.
Traditional security does not operate in the cloud because of the following reasons:
- There is no perimeter to protect
- Manual operations cannot be carried out at the required scale or speed
- Due to a lack of centralization, achieving visibility is incredibly challenging
While cloud computing saves money in the long run, the security component of the jigsaw can eat into the ROI since there are so many moving parts to handle — microservices, containers, Kubernetes, serverless functions, and so on. The famed cybersecurity skills gap is particularly pertinent here, as new technologies emerge quicker than organizations can locate security specialists with relevant experience.
Infrastructure as Code (IaC) is a concept that combines these new technologies by allowing infrastructure to be controlled and provisioned using machine-readable definition files.
This API-driven approach is critical in cloud-first environments because it allows for quick infrastructure changes while also making it easy to program in misconfigurations that leave the environment vulnerable. According to Gartner, misconfigurations account for 95 percent of all security breaches, costing businesses almost $5 trillion between 2018 and 2019.
The greatest vulnerability of all lies behind all of these problems: a lack of visibility. There are hundreds of thousands of instances and accounts in settings as complicated and fluid as the typical enterprise cloud, and understanding what or who is running where and doing what is only conceivable through sophisticated automation. Without it, vulnerabilities caused by misconfigurations can go undiscovered for days, weeks, or even months, or until a breach occurs.
Cloud security posture management tackles these concerns by continuously monitoring cloud risk through prevention, detection, response, and prediction of where risk will occur next.
Benefits of CSPM
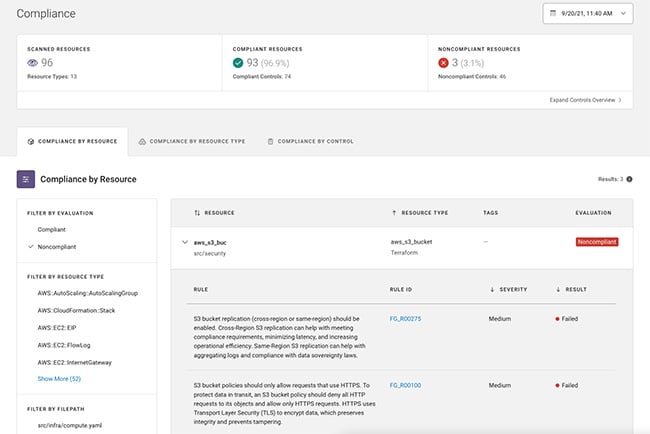
Intentional and unintentional risk are the two categories of risk. The majority of cloud security products concentrate on deliberate: external attacks and hostile insiders. Unintentional errors, such as leaving sensitive data in S3 buckets exposed to the public, can – and can – cause massive damage.
For example, in November 2020, at least 10 million files containing sensitive data belonging to travelers and travel brokers were exposed due to an incorrectly configured S3 bucket. That’s just the latest in a string of high-profile leaks that have afflicted some of the world’s most powerful companies and governments in recent years.
Instead of needing to monitor different consoles and normalize data from multiple suppliers, Cloud Security Posture Management strives to prevent those unintentional vulnerabilities by offering consistent visibility across multi-cloud systems. Misconfigurations are automatically avoided, and time-to-value is shortened.
Because the alerts are sent from a single system rather than six or more, CSPMs reduce alert fatigue, and false positives are reduced thanks to artificial intelligence. As a result, the productivity of the security operations center (SOC) improves.
Because CSPMs are always monitoring and assessing the environment to ensure that compliance regulations are being followed. Corrective procedures can be taken automatically if drift is identified.
Of course, with continuous scans of the entire infrastructure, CSPM discovers hidden dangers, and faster detection implies faster treatment.
The Inner Workings of CSPM
Discovery and visibility, misconfiguration management and remediation, continuous threat monitoring, and DevSecOps integration are all provided by Cloud Security Posture Management:
- Discovery and Visibility Cloud infrastructure assets and security configurations are discovered and visible using CSPM. Across several cloud settings and accounts, users can access a single source of truth. Misconfigurations, metadata, networking, security, and modification activity are all found automatically when the cloud is deployed. A single console is used to administer security group settings across accounts, regions, projects, and virtual networks.
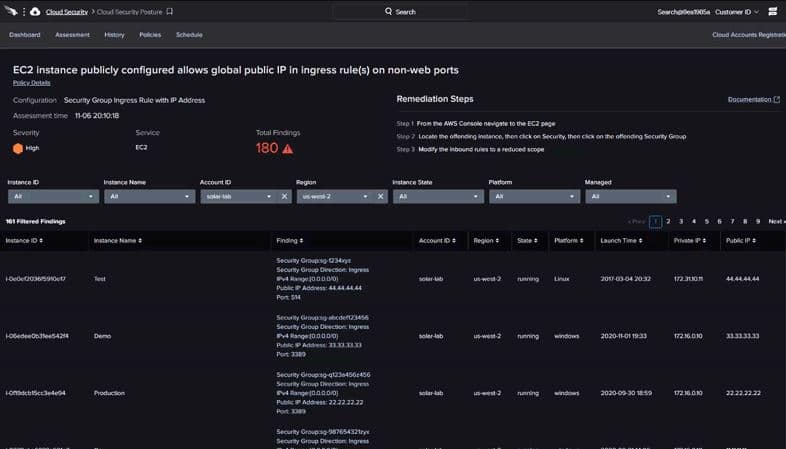
- Misconfiguration Management and Remediation By comparing cloud application configurations to industry and organizational benchmarks, CSPM lowers security risks and speeds up the delivery process, allowing violations to be recognized and remedied in real-time. Misconfigurations, open IP ports, illegal changes, and other issues that expose cloud resources can be corrected using guided remediation, and guardrails are offered to help developers avoid making mistakes. Storage is constantly monitored to ensure that the appropriate permissions are always in place and that data is never unintentionally made public. In addition, database instances are monitored for high availability, backups, and encryption.
- Continuous Threat Detection With a targeted threat identification and management strategy, CSPM proactively detects risks across the application development lifecycle, cutting through the noise of multi-cloud environment security warnings. Because the CSPM concentrates on the areas that adversaries are most likely to target, vulnerabilities are prioritized based on the environment, and vulnerable code is stopped from reaching production, the number of warnings is reduced. Using real-time threat detection, the CSPM will continuously monitor the environment for malicious activity, unauthorized activity, and unauthorized access to cloud services.
- DevSecOps Integration CSPM decreases friction and complexity across many cloud providers and accounts by reducing overhead. Agentless posture management, which is cloud-native, gives centralized visibility and control over all cloud resources. Security operations and DevOps teams will have a single source of truth, and security teams will be able to prevent compromised assets from continuing through the app lifecycle.
To improve visibility and collect insights and context concerning misconfigurations and policy breaches, the CSPM should be connected with the SIEM.
The CSPM should also interact with existing DevOps toolsets, allowing for quicker remediation and reaction inside the DevOps toolset. Reporting and dashboards allow security operations, DevOps, and infrastructure teams to share information.
The best CSPM Tools
Following are some of the popular CSPM tools used by both small and enterprise-level businesses.
1. Aikido
Aikido operates security testing services from the cloud and specializes in the assurance of systems written to run on cloud platforms. As part of the remit, the package includes a CSPM to ensure that the expected host of a new application doesn’t have its own security weaknesses.
The important features of the Aikido platform are:
- A CSPM that checks on cloud platforms and services before a new application is released
- Cloud infrastructure assurance for infrastructure-as-code, containers, and Kubernetes cluster management
- Software composition analysis, dynamic application security testing, and static application security testing
- Assessments of user account structures
- Checks within containers for outdated runtimes
- Can fix some security problems automatically
- Cloud configuration assessments
The Aikido CSPM works with CloudSploit and AWS Inspector in its search for cloud security problems. Each discovery is noted and given a severity score. Many problems can be related and will either be a repetition of the same problem in many different places or a problem in one area that is the consequence of a problem elsewhere. In these cases, the Aikido scan report will group related errors together, this is a deduplication process that focuses attention on root causes.
Pros:
- Examines cloud systems in relation to the new applications that are going to be running on them
- Error reporting that can be channeled through project management automation tools
- Focused, prioritized vulnerability lists that reduce repeated errors down to a unique list
- Interfaces with CloudSploit and AWS Inspector
- User account security
Cons:
- This platform checks on all of the components of a new application and the CSPM is part of that effort rather than being a standalone service
This package is designed for DevOps teams that are creating and managing Web applications and SaaS packages. There are four plan levels available and all include the CSPM. The main difference between the four plans is the capacity of each. You can sign up for assess to a free trial of the Aikido system.
2. Cyscale
Cyscale is a cloud-based subscription package that discovers and maps all cloud assets and then scans for both processes and data stores. The result of this research is formed into a Security Knowledge Graph and that reveals all of the resources and services that a business currently deploys. This system is a live cloud scanner and it can also be integrated into a CI/CD pipeline to provide continuous testing for DevOps teams.
The pertinent features of Cyscale include:
- Identification of data stores for data protection measures
- Assessment of each cloud asset
- A library of cloud asset security best practices
- Comparison of current configurations to the relevant template
- Provides a list of security weaknesses and recommended fixes
- Support security tightening with the formulation of new security policies
- Data privacy standards compliance enforcement
The Cyscale tool scans all of the discovered assets and compares them to usage. This might reveal resources that you are paying for but don’t really need. Thus, the tool is able to save you money. The security scans of your cloud assets extend to APIs, frameworks, and microservices, each of which could well be calling remote services that you don’t even know about.
Each asset is assessed and compared to a known standard of best practices for cloud security. Those standards are stored as templates – there is a library of more than 500 of these in the Cyscale platform. Where possible, you can fix all of the encountered errors with a specific asset by applying the relevant template. If the problem lies with a service that you don’t control, you can take a decision over how to inform the provider of that system to get its security improved.
Pros:
- Flexible cloud-based deployment
- Robust auditing and reporting capabilities
- Extensive support for APIs and Microservices
- Pairs security issues with remediation action
Cons:
- Better suited for larger environments
This security policy system crosses platforms in its searches, looking at AWS, Azure, Google Cloud, and Alibaba Cloud. It checks on virtualizations, networks, serverless systems, databases, services, and applications. The package will tailor its assessments to a given data protection standard. Get started on a 14-day free trial to learn more.
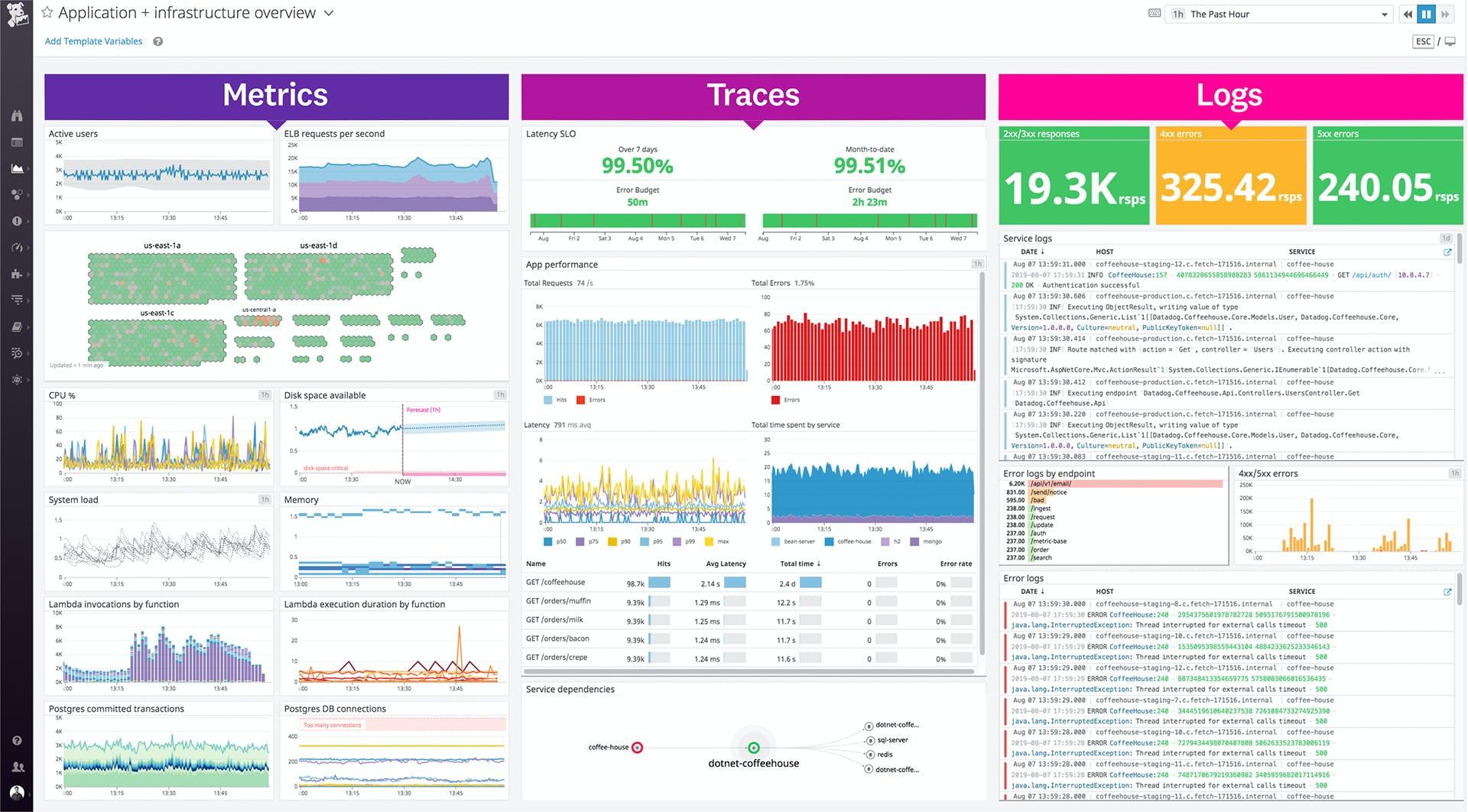
3. Datadog
Datadog monitoring software can be installed on-premises or as a cloud-based service (SaaS). Datadog is compatible with Windows, Linux, and macOS X. AWS, Microsoft Azure, Red Hat OpenShift, and Google Cloud Platform are among the cloud service providers supported.
Its notable features include:
- Provides a single view of an IT/DevOps team’s infrastructure (including servers, apps, metrics, and other services)
- Dashboards that can be customized
- Alerts are sent out in response to important concerns
- Over 250 product integrations are supported
- Logs, latency, and error rates are automatically collected and analyzed
- Allows you to use the API
- Applications built in Java, Python, PHP, .NET, Go, Node, and Ruby are supported
Datadog’s agent is written in Go, and its backend is comprised of Apache Cassandra, PostgreSQL, and Kafka. Datadog uses a Rest Application Program Interface (API) to link with a variety of services, tools, and programming languages.
Pros:
- Excellent graphic options for monitoring multiple metrics
- Highly customizable dashboards, great for NOC teams
- Cloud-based monitoring, can be accessible from anywhere
- 400+ integrations can support nearly any database deployment
- Highly scalable – can work in any size environment
Cons:
- Would like to see a longer trial period
Kubernetes, Chef, Puppet, Ansible, Ubuntu, and Bitbucket are just a few of the integrations available. The user interface features dashboards that may be customized to present graphs made up of numerous data sources in real-time. Datadog may also notify consumers when there are performance difficulties with any set of metrics, such as compute rates.
4. CrowdStrike Horizon
Agentless cloud-native protection that continuously analyses your environment for misconfigurations eliminates security blind spots. CrowdStrike Falcon Horizon provides a single source of truth for cloud resources, giving you total visibility into your multi-cloud environment.
Its notable features include:
- Continuous intelligent monitoring of cloud resources to discover misconfigurations and threats before they become a problem.
- Secure cloud application deployment with increased speed and efficiency.
- Across multi-cloud environments, unified visibility, and control.
- Security concerns are addressed using a step-by-step approach.
- Developers can use guardrails to help them avoid making costly mistakes.
- Threat detection is targeted to reduce alert fatigue.
- Integration with SIEM solutions is seamless.
Pros:
- Excels in hybrid environments (Windows, Linux, Cloud, BYOD, etc.)
- Intuitive admin console makes it easy to get started and is accessible in the cloud
- Can track and alert anomalous behavior over time, improves the longer it monitors the network
- Lightweight agents take up little system resources
Cons:
- Would benefit from a longer trial period
Not only do you obtain useful information and insights into your entire security posture, but you also get advice on how to avoid future security issues.
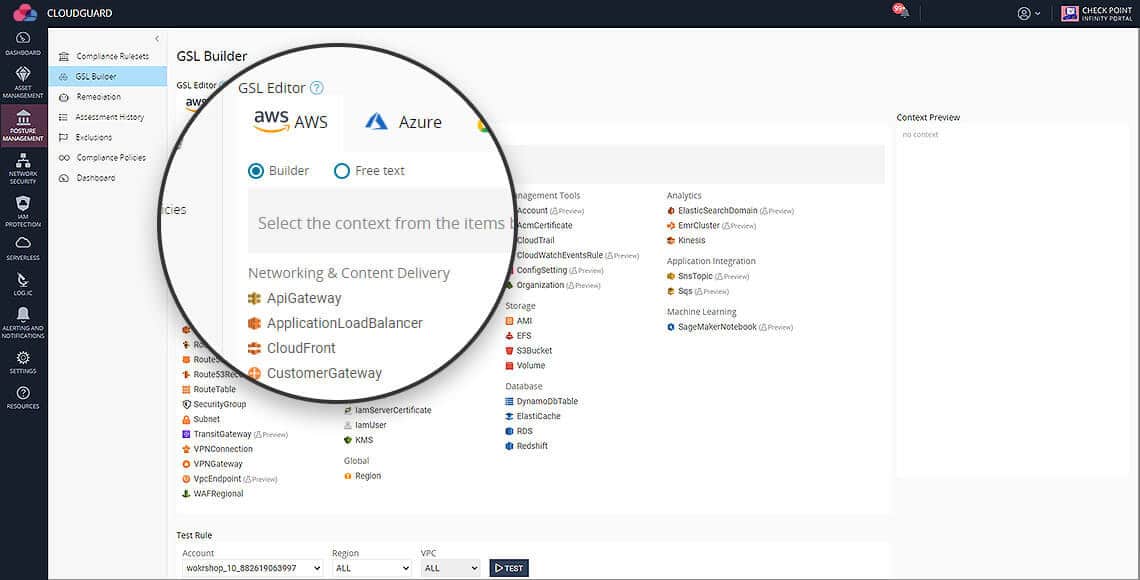
5. CloudGuard Posture Management
CloudGuard Posture Management is an API-based agentless Software as a Service (SaaS) cloud compliance and orchestration platform that automates governance across multi-cloud assets and services as part of the CloudGuard Cloud-Native Security Platform. Misconfiguration detection, security posture assessment, and visualization are among the services offered, as are implementing security best practices and compliance frameworks.
Its notable features include:
- CloudGuard Posture Management allows users to apply gold standard standards across projects, accounts, virtual networks, and regions. Users may see their security posture and target, prioritize, and automatically remediate issues.
- CloudGuard Posture Management guarantees that users follow regulatory standards and security best practices automatically. Users are kept up to date on their security and compliance status through thorough reporting.
- Users can prohibit access to important tasks using privileged identity protection, which is based on Identity Access Management (IAM) roles and users. CloudGuard Posture Management monitors and audits IAM users and roles for unusual behavior regularly.
Pros:
- Focuses heavily on automated workload security
- Uses NIST and CIS benchmarks to help adjust and monitor your security posture
- Offer highly detailed reporting – great for audits
- Offers both continuous and manual scans
Cons:
- Is more advanced than similar tools – can take time to learn
6. Lacework
Lacework is a data-driven cloud security platform that automates cloud security at scale, allowing users to innovate swiftly and securely. Lacework collects, evaluates, and correlates data across an organization’s Kubernetes, AWS, Azure, and GCP systems with pinpoint accuracy, then distills it down to a few key security events. Lacework differentiates itself from its competition by providing automated intrusion detection, security visibility, one-click investigation, and easier cloud compliance.
Its notable features include:
- Lacework keeps companies informed about all activity on all of their cloud platform resources by recognizing new activity in an area, recording changes to policies, roles, and accounts, and informing users.
- Lacework identifies IAM flaws, checks for logging best practices, monitors critical account activities such as unauthorized API calls and ensures secure network configurations to ensure users aren’t missing anything.
- Lacework users may keep their compliance and security up to date by performing a daily re-audit. Lacework analyses account activity for unusual activities regardless of authorized status.
Pros:
- Provides a highly visual look at your risk over different platforms
- The dashboard is simple and easy to navigate
- Can help adhere to compliance requirements such as PCI DSS and HIPAA
Cons:
- Not the best option for managed service providers
7. Fugue
Fugue is a cloud security and compliance platform that secures the full development lifecycle with a unified policy engine powered by the Open Policy Agent (OPA). Fugue gives security and cloud engineering teams more trust in cloud security, allowing them to work more efficiently. Users can use Fugue to perform pre-deployment security checks on CloudFormation, AWS, Kubernetes manifests, and docker files, and receive actionable remedial feedback via developer-friendly tools.
Its notable features include:
- Organizations can apply compliance and security consistently across the software development lifecycle with Fugue’s open-source policy engine.
- By continuously taking snapshots of customer cloud settings to capture comprehensive cloud resource setups, relationships, attributes, and drift, Fugue’s resource data engine provides users with deep visualization and reporting capabilities.
- The Regula policy engine in Fugue helps customers protect their CloudFormation and Terraform IAC at every level of creation and deployment.
Pros:
- Highly customizable interface
- Great reporting dashboards – ideal for NOC teams
- Includes metrics for your cloud development lifecycle
- Supports automated remediation
Cons:
- Better suited for larger cloud networks
8. Threat Stack
By providing full-stack observability, the Threat Stack Cloud Security Platform bridges the gap between development, security, and operations, enhancing overall organizational efficiency for users. The cloud management dashboard, container, host, orchestration, and serverless layers all have observability. Threat Stack enables enterprises to identify known dangers at scale and quickly detect anomalies in their computer infrastructures.
Its notable features include:
- Through absorbing data from AWS CloudTrail, Threat Stack CSPM warns customers of changes performed, such as instances spun up in unused regions.
- Threat Stack’s approach to IAM policies includes monitoring your AWS accounts to ensure that users are following the policies, such as root access and password requirements.
- Users may see an inventory of servers and instances across many AWS accounts thanks to visibility. They may also see important details such as ID, IP, region, type, and so on.
- By scanning configurations across core AWS services, Threat Stack collects information from numerous AWS profiles for users.
Pros:
- Simple yet powerful admin console and reports
- Offers enterprise cloud management tools
- Supports multi-tenant environments
- Leverages AI for threat detection
Cons:
- Better larger environments
9. Trend Micro Hybrid Cloud Security Solution
The Trend Micro Hybrid Cloud Security Solution is a cloud security platform aimed at cloud builders. It provides a comprehensive and unified cloud security solution that makes it simple for users to safeguard cloud infrastructure. The robust security allows customers to make use of the cloud’s benefits and efficiencies for their organizations. Trend Micro Hybrid not only supports all major cloud platforms but also solutions that connect directly into DevOps processes and toolchains.
Its notable features include:
- Trend Micro Hybrid Cloud automates the detection and protection of cloud environments while protecting the network layer, providing simple and adaptable cloud security throughout the migration and expansion processes.
- Trend Micro Cloud One provides application security that is up to date with modern development technologies and techniques, ensuring that your cloud services are protected, detected, and adhere to security best practices.
Pros:
- Supports a wide range of automated threat responses and alerting templates
- Centralized management for a simple view of your device security
- Offers advanced reporting capabilities as well as automated audits
- Is FIPS 140-2 Certified
Cons:
- Better suited for larger networks
10. BMC Helix Cloud Security
BMC Helix Cloud Security automates cloud configuration security checks and remediation without requiring any coding, allowing services like Infrastructure as a Service (IaaS) and Platform as a Service (PaaS) to have a secure and consistent setup with an audit trail. By integrating compliance and security testing into service delivery and cloud operations, BMC Helix Cloud Security improves governance and reduces risk. Its key features are:
- For users who employ Center for Internet Security (CIS) policies for cloud assets, BMC Helix Cloud Security automates cloud security posture management.
- Self-driving remediation, automatic remediation via an easy UI, and custom remediation support are all features of the software that make the repair process easier for users.
- BMC Helix Cloud Security includes policies such as CIS, GDPR, and PCI. Custom policies are also supported by BMC Helix.
Pros:
- Simple yet intuitive interface
- Can automated security tasks such as vulnerability scans, and automated network probes
- Can automate configuration restoration
- Can support multi-cloud and hybrid cloud environments
Cons:
- Better suited for larger networks, especially those with in-house remediation teams