Email continues to be the most commonly targeted attack surface for both small and enterprise-level networks. Phishing and other forms of corporate email compromise are on the rise as hackers seek to access your company’s sensitive data through email. Using an Email Security Solution is your first line of defense against hackers, spam, and viruses.
Here is our list of the best email protection software:
- Guardz – EDITOR’S CHOICE This email protection system is based in the cloud and plugs into Gmail and Exchange Server/Outlook systems to spot spam, phishing, BEC, and malware. Get a 14-day free trial.
- SolarWinds Server & Application Monitor – FREE TRIAL This on-premises package watches over application operating efficiency for applications, such as Active Directory and Exchange Server. Runs on Windows Server. Download a 30-day free trial.
- Endpoint DLP Plus – FREE TRIAL Endpoint DLP Plus is renowned for its strong email protection capabilities, efficiently safeguarding sensitive data against leaks and unauthorized access through corporate email channels. It stands out for integrating advanced email filtering and data loss prevention, making it a top choice for organizations concerned with email security. Start a 30-day free trial.
- SolarWinds Identity Monitor Protect account credentials in Active Directory, which operates for Exchange Server as well as system access. Runs on Windows Server.
- Proofpoint Email Protection Software This cloud-based system uses AI to filter out spam, phishing, BEC, and malware.
- MDaemon’s Security Gateway This cloud-based service scans incoming emails for spam, malware, and threats such as BEC and phishing and implements data loss prevention on outgoing emails. An on-premises option runs on Windows Server.
- Mimecast Email Protection Software This cloud package leverages an impersonation detector and a global database of threat indicators to block malicious emails.
- MailGuard Email Protection Software This cloud service combines email scanning with DDoS protection and spyware blocking.
- Microsoft Defender for Office 365 This cloud-based service from Microsoft can protect Outlook and Exchange Server from spam, phishing, and other email-based attacks.
- Cisco Cloud Email Security Delivered from the cloud, this service filters out scams and attacks and provides reporting for threat analysis.
- Barracuda Total Email Protection This cloud package encrypts emails for protection across the internet and provides threat scanning, DDoS absorption, and malware blocking.
Various Email Security Gateways are available. For some, the goal is to provide granular administrative control and enhanced capabilities to business users. Smaller companies seeking an easy-to-use platform with a reasonable pricing range may want to consider one of these options. Security is at risk due to malicious cyber activities. There are many other types of scams out there, including spoofing and spear-phishing, ransomware, identity theft, and impersonation.
We’ve compiled a list of the best email security software for your privacy’s sake. These technologies aid in the detection and prevention of assaults, preventing them from causing any harm or obtaining critical information. Companies are now employing the following tools to secure their corporate data. SolarWinds® Identity Monitor comes out on top in this comparison. With this email security application, you get the best of both worlds: flexibility, usability, and sophistication. Consider the options and choose one for your company’s email security.
The best Email Protection software
1. Guardz – FREE TRIAL
Companies that use Microsoft 365 or Google Workspace for their office productivity services can get the Guardz platform to protect their email service and cloud drives. This is part of the full Guardz package, which includes endpoint security, Dark Web scanning, and employee awareness training.
Here are the most important services for email protection in the Guardz bundle:
- Hosted in the cloud
- A per-user subscription price
- A console that can be accessed through any standard Web browser
- Automated operations without the need for on-staff security experts
- Intercepts spam, phishing, business email compromise, and malware
- Email quarantining with the option to manually restore suspected messages
- Dark Web scanning to look for disclosed lists of email addresses
- A phishing email simulator
- Employee awareness training courses
The administrator console of the Guardz system maintains a record of all detection events and provides access to the quarantine area. This enables managers to examine removed emails and assess them for effective classification. The system is likely to sometimes quarantine valid emails and these can be restored.
The Guardz system needs to be managed by a managed service provider and the company offers a list of recommended MSPs. Guardz also offers a managed security service plan.
You can register for a 14-day free trial.
EDITOR'S CHOICE
Guardz is our top pick for email protection software because it removes spam, malware, phishing, and business email compromise attempts without any calibration or rule creation needed by technicians. The system is hosted in the cloud and it moves malicious emails into quarantine where they can be analyzed. The Guardz package includes a phishing simulator to test the system and educate users and it has a library of video-based employee awareness training courses.
Download: Get a 14-day FREE Trial
Official Site: https://guardz.com/free_trial
OS: Cloud-based
2. SolarWinds Server & Application Monitor – FREE TRIAL
Server and application uptime may be improved using SolarWinds Server & Application Monitor, one of the finest systems management tools. Server health and network traffic may also be kept track of using this well-known utility. An application supporting infrastructure may be monitored using SolarWinds Server & Application Monitor.
The following are some of the most important aspects of the product:
- Compatibility between hardware
- It is compatible with a wide range of operating systems, including Windows Server, Linux, Unix, Solaris, and HP-UX
- Playable scripts may be written by the user
- Supports vulnerability assessment and monitoring
- Reveals more about the situation.
- Improved response time to problems
- Reduce the likelihood of unplanned and expensive downtime
- Performance monitoring in real-time
- Inexpensive and easy to use software for System Management
The cost-effective and easy-to-use solution provides a wealth of information about an application and identifies server faults. Server & Application Monitor from SolarWinds can help you find and fix sluggish apps and servers in your IT environment.
In all, SolarWinds Server & Application Monitor can keep track of the actions of more than 1,200 distinct apps. Application Dependency Mapping, Customizable Monitoring, quicker troubleshooting, and more are all included. In addition to 1200+ templates, SolarWinds Server & Application Monitor gives you access to Active Directory, Java, Skype for Business, and Office 365 email. The tool is very useful, cost-effective, and time-saving for management.
Click here to download and start using this tool.
3. ManageEngine Endpoint DLP Plus – FREE TRIAL 
Endpoint DLP Plus shines with its robust email protection capabilities, designed to safeguard sensitive data from leakage and unauthorized access through corporate email channels.
Key Features:
- Advanced Email Filtering: Scans and filters emails to prevent sensitive data exposure.
- Data Loss Prevention: Monitors and blocks the transfer of sensitive information via email.
- Real-Time Alerts: Provides instant alerts on suspicious email activities, enhancing security response times.
- Encryption: Secures emails by encrypting sensitive data sent from corporate accounts.
- Policy Enforcement: Allows administrators to set comprehensive policies for email usage and data protection.
- User Activity Monitoring: Tracks and logs email activity to detect and respond to policy violations.
Why do we recommend it?
Endpoint DLP Plus is particularly adept at integrating data loss prevention with email security, ensuring that sensitive data does not leave the corporate network without authorization. Its real-time monitoring and alert system enable quick responses to potential data breaches, significantly reducing the risk of data loss.
Who is it recommended for?
This tool is ideal for IT security teams in organizations of all sizes that prioritize the security of their email communications. It is especially useful for businesses that handle large volumes of sensitive information and need to comply with regulatory requirements regarding data protection.
Pros:
- Robust Email Security: Offers comprehensive tools to protect against data leaks via email
- Real-Time Monitoring and Alerts: Ensures immediate response to unauthorized data transmissions
- Strong Encryption: Encrypts emails to protect data integrity and privacy
- Customizable Policies: Provides flexible settings to meet the specific security needs of any organization
- User Activity Logs: Helps in forensic analysis by logging detailed email activities
Cons:
- Complex Policy Configuration: Setting up and managing policies can be complex and time-consuming
- Resource Intensity: May require significant system resources to maintain optimal performance
4. SolarWinds Identity Monitor
Using a web-based application, SolarWinds Identity Monitor alerts users when their corporate credentials are compromised. Account TakeOver (ATO) assaults, corporate domains, and individual IDs are all monitored closely to ensure they aren’t compromised in a data breach. The interface of the email security solution is straightforward to use, making it simple for users to find the buttons they need. The user-friendly design also aids in keeping tabs on all email addresses. As a consequence, the program warns the administrator once the credentials are found in a data breach. Additionally, it aids with password resets and the scanning of recent logins.
The following are some of the most important aspects of the product:
- IP Address traceability
- Verifies the ownership of a domain name
- Creates a watch list of email domains to safeguard login credentials
- A user-friendly dashboard with a simple menu structure
- Allows for monitoring of numerous domains at once
- Supports monitoring of private email messages
- Faster responses
In a data breach, SolarWinds Identity Monitor may monitor numerous domains for possible exposure. This aids in the early detection of the assailants. In addition, the chronology shows any past breaches that have occurred. In addition to credentials, SolarWinds Identity Monitor gives password encryption type, account registration time, and any personal data connected to a data breach. Generally speaking, SolarWinds Identity Monitor is an email security solution that is both effective and scalable.
5. Proofpoint Email Protection Software
Proofpoint is the world’s largest email security provider and a market leader in email security gateways, generating over $1 billion in sales annually. Proofpoint Essentials is the company’s answer to the needs of small and medium-sized businesses. Using a single platform, Essentials provides email security, encryption, and archiving, as well as email continuity and disaster recovery. Using Proofpoint’s global threat intelligence platform, they have an unprecedented view of email threats across email, social media, and mobile.
The following are some of the most important aspects of the product:
- Leverages AI to prevent email fraud
- Protects from phishing scams, BEC, and malicious payloads
- Can detect scams based on language, providing even more protection
- Supports tagging highly suspicious emails versus junking them
- Offers granular controls for both end-users and sysadmins
Third-party threat information is used by certain other providers and may not be as accurate. Emails from more than 100 million mailboxes, 200 million social media accounts, and seven mobile applications are collected and analyzed by Proofpoint every day. Proofpoint protects more than half of the Fortune 100, five of the world’s top banks, and seven of the world’s top ten retailers.
Proofpoint provides the greatest security against email threats, with comprehensive spam prevention and detection, robust URL defense, and dynamic content filtering. Many of the capabilities that would ordinarily be pricey add-ons, such as archiving, are included as part of the Professional package in Essentials. Essentials offers a variety of statistics and logs to help you better understand and administer your email network.
Granular controls and better threats are reported in Proofpoint’s admin panel. Enterprise-level email security at an affordable price is provided by Proofpoint Essentials. It’s a perfect option for enterprises and MSPs, with simple setup, deployment, and low prices. If you’re working with MS Office 365, Proofpoint’s Azure Active Directory Sync makes it easy to add new users and keep existing ones updated.
6. MDaemon’s Security Gateway
Screenshot for SecurityGateway for Email Servers
MDaemon’s Security Gateway is a robust email security product that uses tried-and-true security methods. It uses a variety of security measures to keep harmful assaults out of the message flow on several platforms, including Microsoft Exchange and Office 365. Various anti-virus engines, heuristic analysis methods, and signature recognition are all supported by the platform to safeguard your private information from intruders.
The following are some of the most important aspects of the product:
- Offers a full reporting system
- DLP and custom rule filtering are supported
- Preparation of quarantine reports
- Customizable setup and design
- Administering it is simple
- Whitelisting/blacklisting
- Various methods of reduction
- Preventing Data Leaks
- Automatically redirects HTTP requests to HTTPS
- SSL and TLS encryption are supported
- Compliance with the rules
- Retaining and archiving
- Spam Detection
- Encryption
- Multiple languages are supported
- Customizable user interface
- Email archiving is a supported feature
- Bandwidth limitation
- Detailed Logs are available
It uses the most advanced technology to ensure that there are no false positives. The tools also include a spam-blocking engine capable of detecting 99 percent of spam. Using MDaemon’s Security Gateway, you can defend yourself from both internal and external email threats.
The detailed logs and comprehensive reports it provides on email traffic, both incoming and outgoing, are another perk. Compared to other email security software, it is one of the most affordable options on the market. Automate procedures like adding domains or users by using basic and easy-to-use parameters.
Quick deployment of the policy enforcement tool is possible. As a result, IT staff are free to work on other projects since they know that email security technology keeps an eye out for dangers and intervenes when necessary.
7. Mimecast Email Protection Software
Mimecast is one of the most comprehensive email security gateways available. It’s designed particularly for business customers, who may make use of the advanced threat prevention and fine-grained administrative controls it provides. The Mimecast platform has a lot of capability and can be tailored to suit your needs. Mimecast is a powerful email security solution that can be customized to meet your requirements. The Impersonation Protection feature of Mimecast may help keep you safe from phishing scams. In addition, Mimecast provides capabilities like attachment and URL security. These prevent attacks from invading your network in real-time.
The following are some of the most important aspects of the product:
- DNS authentication services
- Dashboard for threat intelligence
- Eliminates threats
- Prevents impersonation attacks by detecting phishing attempts
- Anti-malicious attachments are protected
- Protects against URLs that are harmful to the user
- Multiple detection methods are supported
- There’s no need to set up any software
- Grainy control is provided
Threat research is one of Mimecast’s strengths. Hundreds of millions of emails are scanned daily, and a massive danger database is maintained. As a result of this, consumers can rest certain that they are constantly aware of the most recent risks and are prepared to safeguard their businesses from them. Mimecast’s reporting and analytics are often praised by customers.
As a result, you can monitor the security of your emails and the performance of Mimecast with ease. It has a low rate of erroneous spam detection and a high rate of filtering spam and viruses. In the case of large enterprises, Mimecast is an excellent choice for email security.
8. MailGuard Email Protection Software
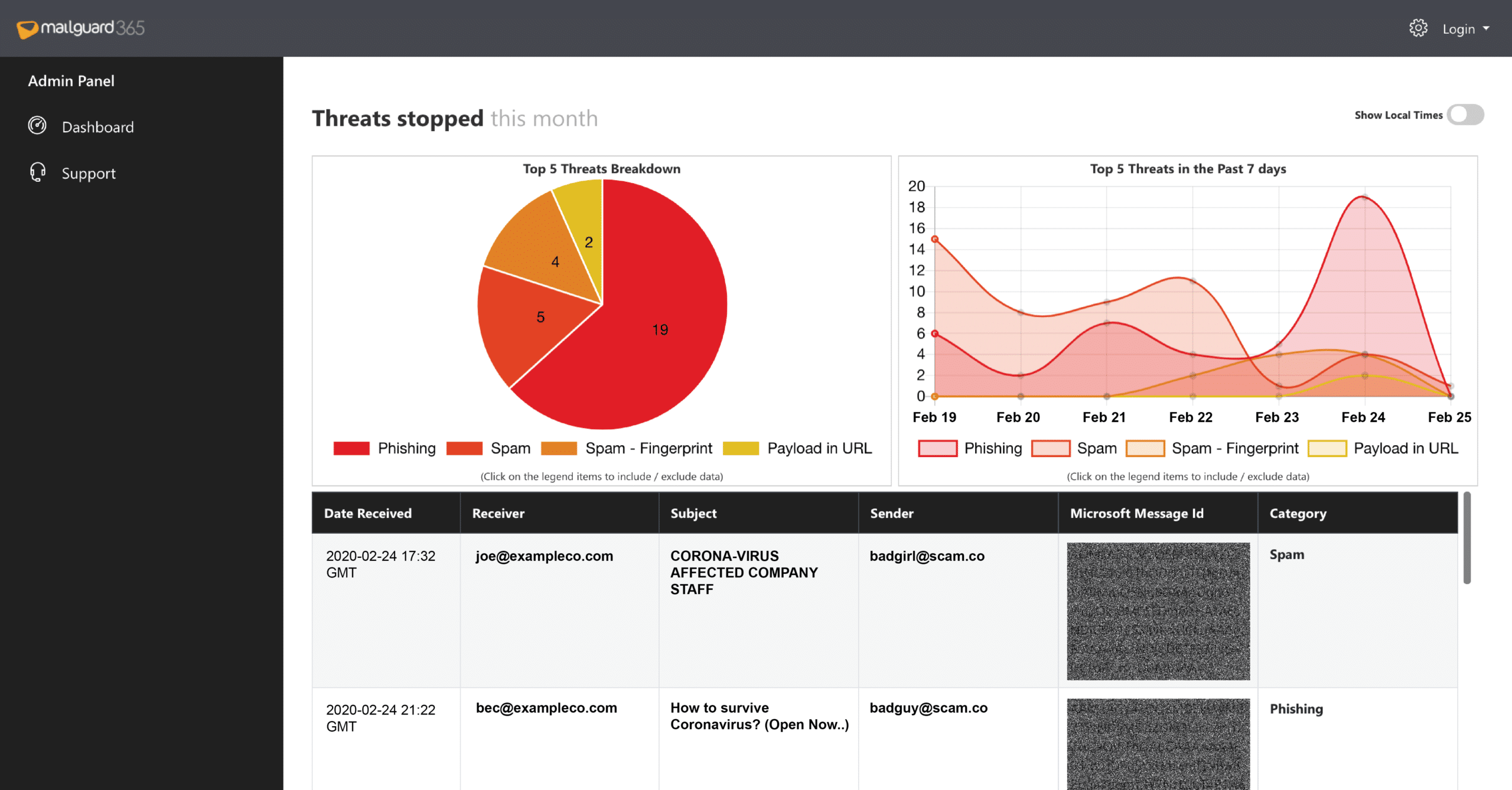
One of the most popular cloud-based email security software on the market is MailGuard. Hybrid AI (Artificial intelligence) threat detection engines identify any new or upcoming threats. Customers are protected immediately since the email security technology predicts or anticipates any danger.
The following are some of the most important aspects of the product:
- Architecture for large-scale use of the cloud
- Active heuristic filters are supported
- Anti-spyware scanners
- Anti-DDoS measures
- Protection of incoming material
- Protection against data leaks
- Allows for the enforcement of outbound policies
- Complaints handling
- Compatible with any email service provider
- Email activity reports are available
- In and outbound email traffic may be seen in full detail
- Availability of customer service representatives around the clock
- Encryption of email
- Spam Assassin
- Whitelisting/blacklisting
- Data mining for human behavior
With MailGuard, you don’t need to install any extra software. MailGuard has a staff of experts ready to assist you around the clock. You’ll always have access to the latest security upgrades and round-the-clock assistance from MailGuard Email Security Software.
As a SaaS service, it offers high levels of security at a reasonable cost. No software licenses are needed. Software deployment into current on-premise or cloud-based services often takes just a few hours. Emails are safeguarded in a rapid, redundant, fault-tolerant, and dependable manner. Access detailed email use stats and several spam filters to safeguard your private information. Scams, viruses, spyware, malware, ransomware, spear phishing, and other cyber threats may all be prevented using MailGuard.
9. Microsoft Defender for Office 365
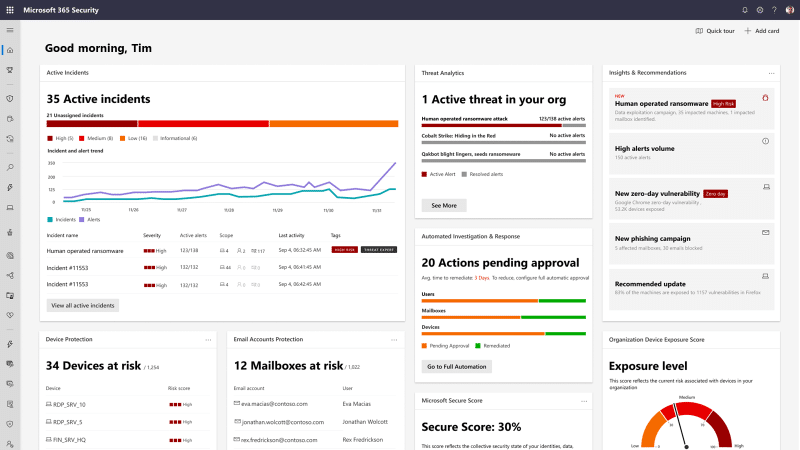
Cloud-based email filtering services like Microsoft Defender for Office 365 function seamlessly with Office 365, as expected from a company like Microsoft. Using anti-virus and URL scanning helps keep enterprises safe against malicious code and infections they haven’t seen before.
The following are some of the most important aspects of the product:
- Supports hybrid deployment options
- Integrates well into your Teams environment
- Produces real-time threat reports
- Offers administrator’s granular control over their protection policy
- Offers a tier with attack simulation training
All attachments are protected against phishing and malware using Microsoft Defender’s anti-malware security for Microsoft OneDrive as well as the cloud-based Microsoft Teams platform. Customers of Office 365 will have no trouble getting up and running.
Defender offers administrators with threat protection rules, reporting, and investigation and response capabilities that organizations would not otherwise receive with Office 365 as a supplementary service to increase security for Office 365.
With Defender, administrators may establish threat protection, monitor real-time information, and utilize tools to analyze attacks and where they originate. This is a critical feature that goes above and beyond what organizations can do with Office 365 in terms of security.
Despite these capabilities, Office 365’s spam filtering, admin features, and phishing prevention are not as advanced as the other third-party solutions we’ve covered on this list. Customers choose Microsoft Defender because it is a complete solution that integrates seamlessly with Office 365.
10. Cisco Cloud Email Security
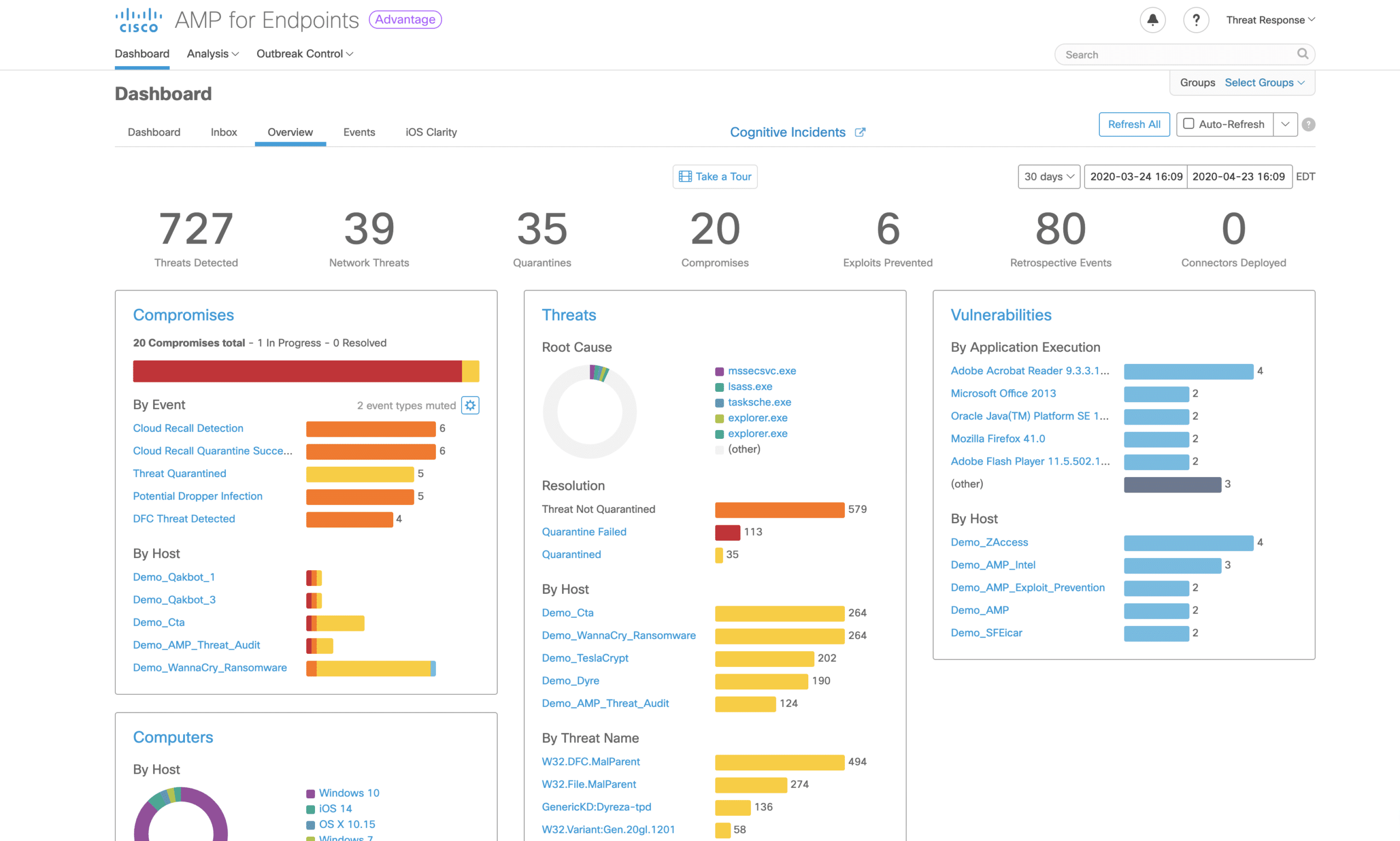
To prevent corporate email compromise and phishing assaults, Cisco has developed an email safe gateway that is highly resistant to these threats. As a result, you can always expect the most up-to-date email threat protection from their extensive research team.
The following are some of the most important aspects of the product:
- Offers automated threat response against phishing, scams emails, and malicious attachments
- Provides a high-level view of attacks across your domain
- Takes a multi-layered approach when defending against email-based threats
- Integrates with a wide range of other security platforms
When it comes to ransomware and compromised corporate email, Cisco’s platform is an excellent place to start. As a result of a security mechanism that immediately blocks links it considers hazardous, emails that seem authentic are secure. Customizable admin options may be found on this platform. The reporting and logging features available are powerful and give you valuable information about the security of your email.
Cisco’s spam filtering is excellent, so you’ll only get the emails you want. In addition, the platform provides techniques to verify that your emails are encrypted to prevent data loss.
As a Cisco product, this platform can simply be incorporated with the company’s other security offerings. Multi-layered protection is now available for your organization. Larger organizations could benefit greatly from this service, and we’d be happy to pass it along.
11. Barracuda Total Email Protection
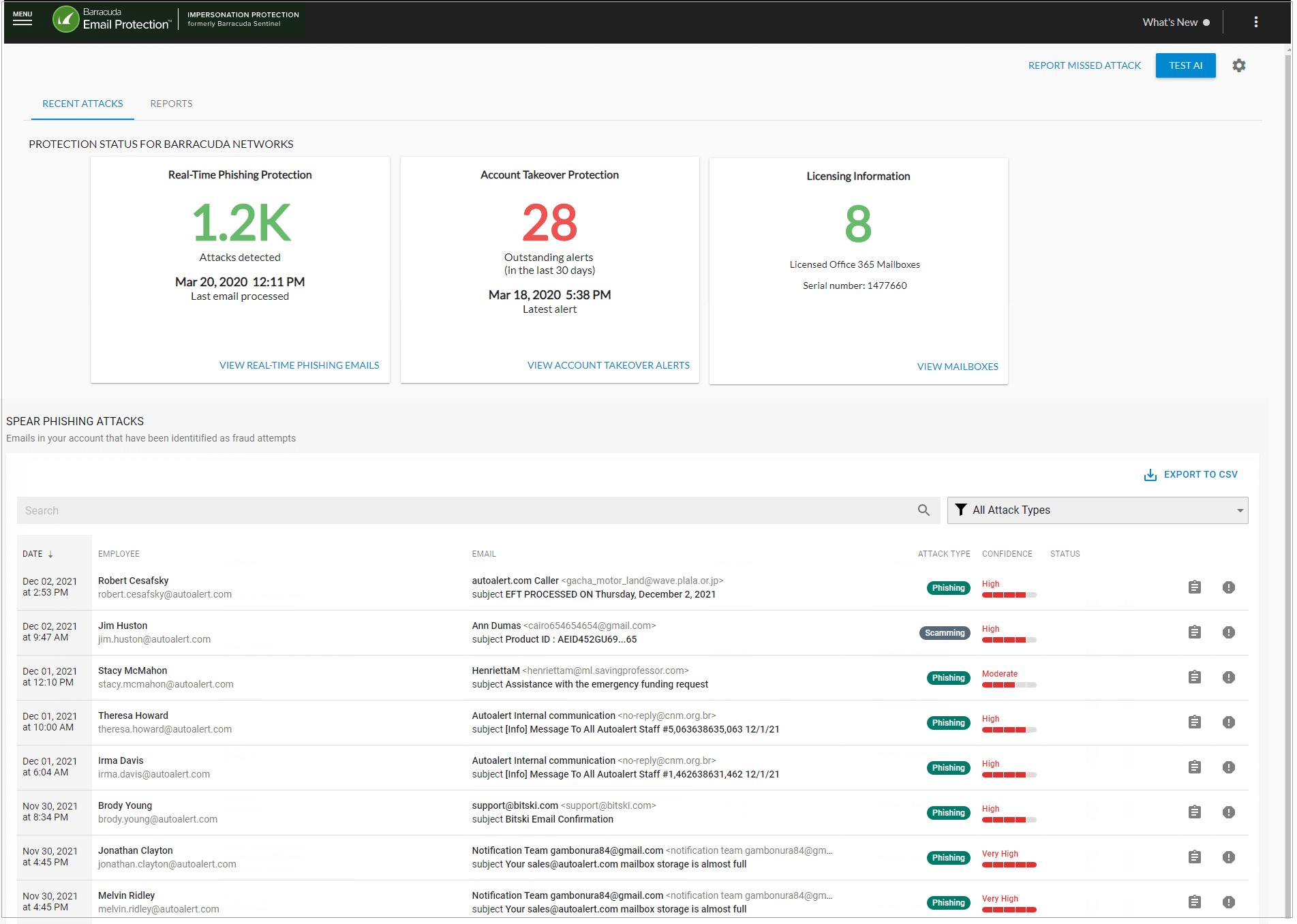
Email attackers are increasingly resorting to social engineering techniques to get around email security. Most businesses use Barracuda Total Email Protection to remain one step ahead of these fraudsters and catch them in the act.
The following are some of the most important aspects of the product:
- Encryption of electronic mail
- Filtering of spam is supported protection against malware and typosquatting
- Enhanced anti-threat measures
- Protection against phishing anti-DDoS protection
- Filtering of outgoing email
- Uncovers Employee impersonation
- Stops anti-spyware
- Exportable reports are available
- Security warnings for account takeovers
- Automated DMARC reporting
- Filtering of online content
- Provides backup from one cloud to another
All 13 categories of email danger are addressed by this physical gadget, which is hooked into your network. To stop dangerous emails, our hybrid cloud system gathers all incoming email traffic before an attack. Viruses, spam, phishing attempts, and harmful attachments may all be eliminated by the email security program.
Use outbound content verification to ensure that you aren’t leaking confidential information. The tool does not need the installation of real equipment. Email security software may also be installed on a virtual server in AWS or Azure and operate in the cloud. Email encryption and flexible deployment options are available for an extra layer of protection, so make use of them.
Multiple layers of protection are necessary for email security. Even with an email gateway in place, corporate email accounts are still vulnerable to attack. As a result, Barracuda Total Email Protection was launched to safeguard your organization, data, and workers from any breach. It’s an excellent defensive solution with AI-enabled inbox protection. As a result, they can identify threats in real-time.
Final Thoughts
The greatest email security tool is SolarWinds Identity Monitor. The program has a wide variety of features and an easy-to-use interface. At a reasonable price, this beginner-friendly application provides an enterprise-level experience.
Numerous sellers provide high-quality tools but can’t be depended upon to keep their costs the same. For years, SolarWinds has consistently produced some of the top IT products for businesses networks. Its product line is trustworthy, and it has excellent customer service to back it up. Identity Monitor is a great option for most networks in terms of email security software.
Viruses, spam, malware, ransomware, and phishing are just a few of the risks on the rise in the business world. A well-known and respected email protection software is the best way to protect your data.
Check out some of the world-class email protection software described above that can safeguard your important data from such dangers. Check them out. Before making a decision, examine the pros and cons of several tools and pick the tool that best suits your risk tolerance and needs.