Businesses are expanding their reach by empowering mobile employees located in different parts of the world to access company data and apps using any device of their choosing. The present endpoint antivirus and Virtual Private Network (VPN) technologies are incapable of preventing sophisticated threats. This is because users and apps are relocating to areas that are beyond the conventional network boundary. This presents a dilemma for security teams, who now need to maintain visibility into network traffic while also ensuring the safety of mobile workers.
The preventative capabilities of the Security Operating Platform may now be made available to mobile workers, regardless of where they are located, thanks to GlobalProtect. Greater visibility into all traffic, users, devices, and apps is provided by GlobalProtect as a result of its utilization of the capabilities of a next-generation firewall. It is possible to increase your organization’s security by implementing policies that are uniform across all users, therefore removing blind spots caused by remote access.
GlobalProtect makes it possible for security policies to be applied consistently to users irrespective of their location and gives complete visibility into the traffic of all applications across all ports. It provides mobile employees with a transparent layer of protection by utilizing a secure connection that is constantly active. You can prevent risks such as phishing and credential theft from stealing vital company data and information with the help of GlobalProtect.
If you need a VPN for your office, then GlobalProtect might be the service that best meets your needs. The solution allows you to access business data regardless of where you are located by extending the security controls to all sites. This program protects against phishing attempts and other forms of credential theft by maintaining a secure connection at all times. In addition to this, the program provides in-depth insights and policies for limiting access to network resources to the requirements of a business. It is simple to install and administer, and you can even control the security policy for your staff members.
Following the successful installation of the program, it will immediately begin operating in the background and will offer your users a secure connection. It is simple to administer using BITS, and you ought to be able to exercise control over how it is used by making use of the concealed icons. You also have the option to manually enable the GlobalProtect client by using the GUI that it provides. It functions most effectively for businesses that own a sizable IT infrastructure and a predetermined user population.
Implement a Zero Trust Architecture
Whether they are connecting from inside or outside the enterprise, users can create exact restrictions through the use of GlobalProtect that can limit or allow access depending on the requirements of the business. It gives you the ability to implement granular access control based on the compliance state of each user and device, as well as providing authoritative user and device identity. Find out more about the concept of zero trust.
Visibility and Control
It is important to GlobalProtect that those administrators have access to a console that is aesthetically pleasing so that they can better perceive and keep an eye on network connections. There is an abundance of data that can be accessed yet, there is only a little amount of data that can be accessed regarding remote devices. When exploring the dashboards, you will see that there is only one view accessible for devices that are placed outside the four walls of the workplace.
Enable and Secure Bring-Your-Own-Device (BYOD)
You can apply individualized levels of access control to corporate, BYOD, and third-party devices when you use GlobalProtect. GlobalProtect offers granular application access to on-premises and cloud-based corporate applications for any devices, including bring-your-own-device (BYOD) and third-party hardware. It enables automatic detection of unmanaged devices as well as access control for such devices.
Prisma Access by Palo Alto Networks offers dependable network protection for any users and applications that traverse your distant networks. Users are provided with secure access to the internet as well as apps hosted in the cloud and data centers while using Prisma Access. In addition to this, the solution consolidates all of your networking and security capabilities into a single cloud-delivered platform, making it possible for hybrid workforces to be both agile and adaptable.
Prisma Access can be managed in two ways:
- Cloud Managed
- Panorama Managed
Prisma Access delivers both networking and security services, including:
- SD-WAN
- VPN
- Zero Trust Network Access (ZTNA)
- Quality of service (QoS)
- Clean Pipe
- Firewall as a service (FWaaS)
- DNS Security
- Threat Prevention
- Cloud Secure Web Gateway (SWG)
- Data Loss Prevention (DLP)
- Cloud Access Security Broker (CASB)
Prisma Access by Palo Alto Networks Features:
- App-ID, User-ID
- Device-ID
- SSL Decryption
- Dynamic User Group (DUG) Monitoring
- AI/ML-Based Detection
- IoT Security
- Reporting
- URL Filtering
- Enterprise Data Loss Prevention (DLP)
- Digital Experience Monitoring (DEM)
- Logging, Policy Automation
- Intrusion Prevention System (IPS), and many more
Prisma Access by Palo Alto Networks Benefits:
- Security Prisma Access provides you with dependable protection against cyberattacks by enforcing security policies everywhere you go. You will also acquire the security that works to block known and undiscovered malware, exploits, credential theft, command and control, and many more attack vectors across all ports and protocols when you implement Prisma Access. This protection is included as part of the Prisma Access package.
- Global connectivity Through the utilization of its networking layer, Prisma Access offers worldwide coverage.
- Scalability Prisma Access features automatically controlled scalability that is both adaptable and agile, and it scales to meet your needs.
- Instant deployment The deployment process is quick, which eliminates the need to waste time configuring a solution, operating it, or shipping hardware to get started. This frees up valuable time that can be used for other purposes.
The top alternatives to GlobalProtect
1. Check Point’s SASE – ACCESS FREE DEMO
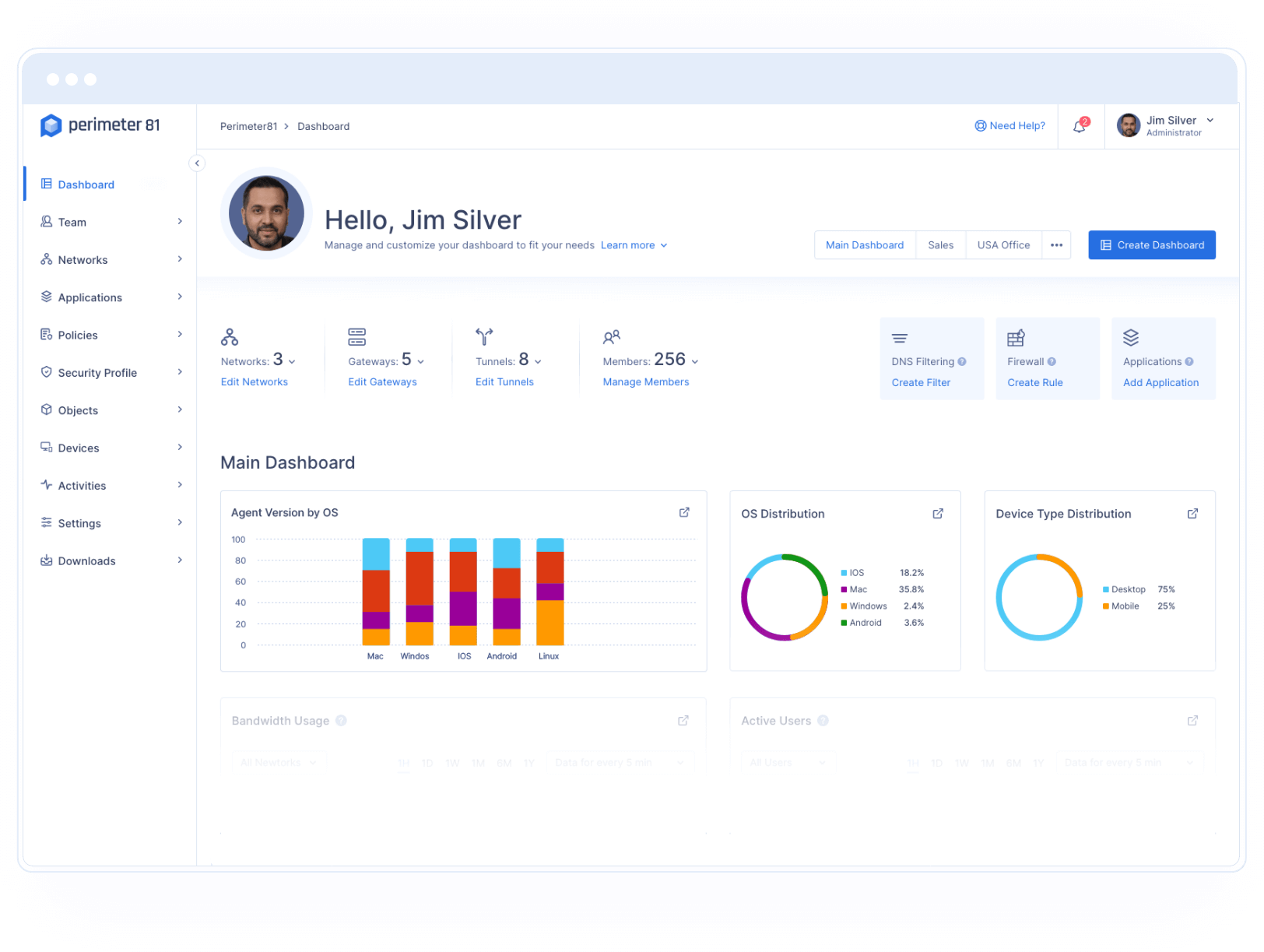
The usage of network security by businesses is undergoing a sea change as a result of the introduction of Check Point’s SASE (formerly known as Perimeter 81), a Software-as-a-Service (SaaS) solution that offers customized networking and the greatest degree of cloud protection. Check Point’s SASE is an integrated solution that enables businesses of any size to be mobile and cloud-confident in a secure manner. This solution streamlines the process of gaining access to a secure network, cloud, and applications for a modern and distributed workforce.
The user-focused, cloud-based Secure Network as a service offered by Check Point’s SASE is not comparable to traditional VPN and hardware-based firewall technologies. It employs the Software-Defined Perimeter and the Zero Trust security paradigms respectively. It provides enhanced insight into the network, easy connectivity with the industry’s leading cloud providers, and automated onboarding. Begin by registering for a free demo.
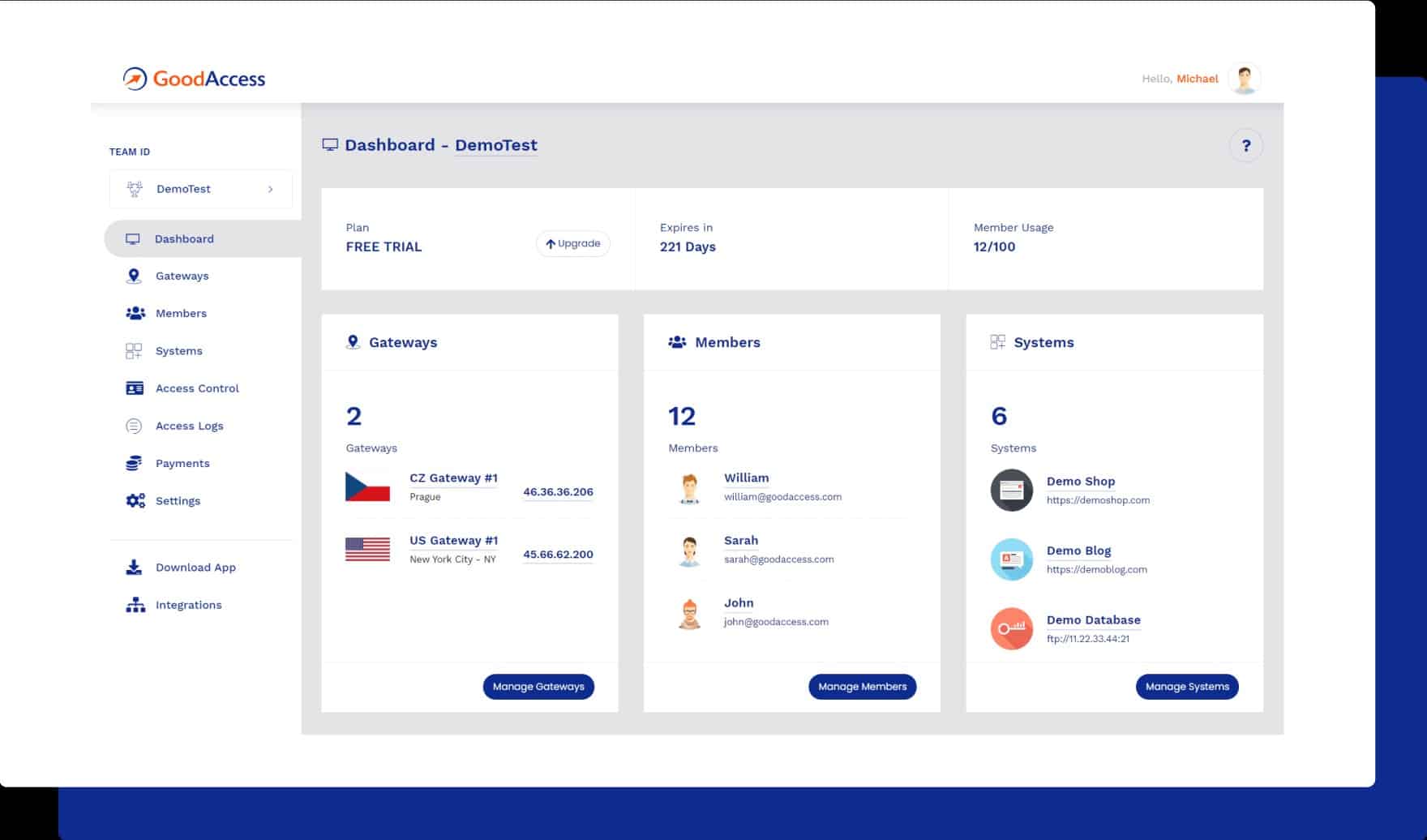
2. GoodAccess
GoodAccess is a cloud-based VPN that enables users to set up a secure virtual network (Software Defined Perimeter) with identity-based access control in a matter of seconds rather than minutes. This solution is perfect for small and medium organizations that wish to link their offices to their remote workers, apps, and data centers safely and securely. The deployment of a private gateway that has a dedicated static IP can be accomplished with the help of GoodAccess by businesses. In addition to this, they offer a web dashboard that is simple to grasp for managing people, devices, and access permissions (SSO, Google, Azure), they unify two-factor authentication and multi-factor authentication at the network level, and they employ access logs to boost network visibility.
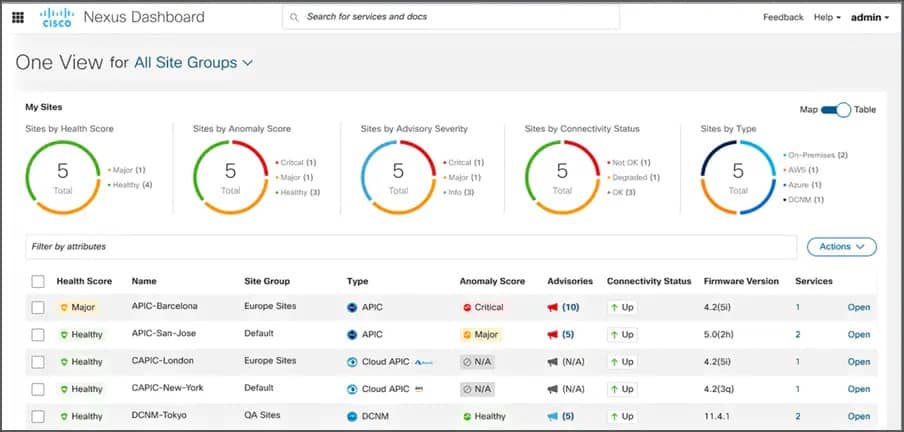
3. Cisco AnyConnect
Workers at a distance have VPN access. Access to the company network is seamless and extremely secure for remote workers. This will enable people to work from any device and any place at any time. It will also safeguard the organization. Cisco Secure Remote Worker is a system that offers remote employees enhanced security. It enables users to work from any device and any place at any time. Cisco can assist you in accelerating the performance of your organization by delivering flexible, policy-driven access that supports remote employees through wired, wireless, and VPN connections. With several options that go beyond typical VPN capabilities, you can get more for less and provide more secure access to distant workers. You may obtain visibility and control over your distributed organization by seeing which users and devices connect to the network.
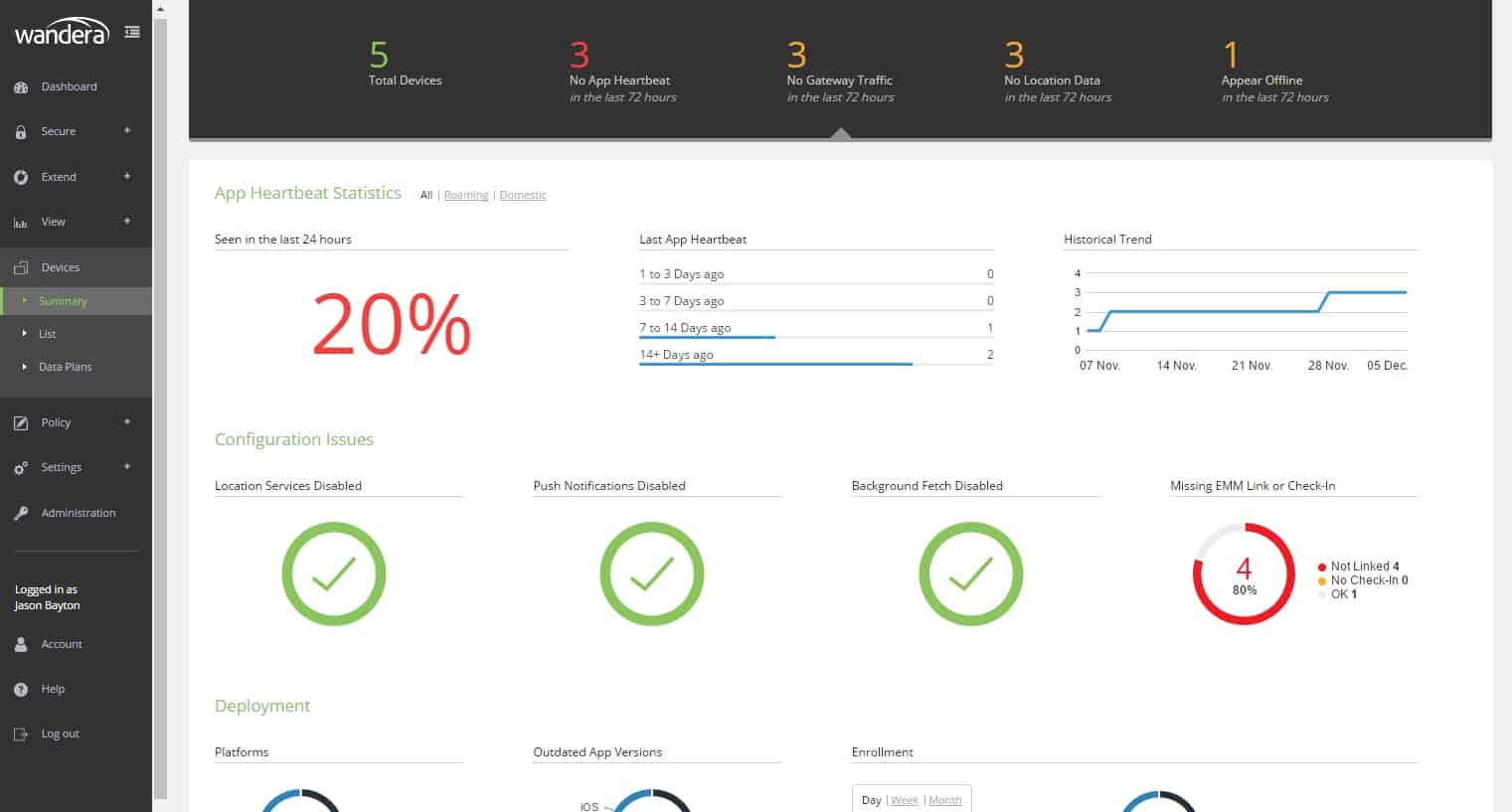
4. Wandera
Real-time security that is unified and protects remote users from danger, regardless of where those users are located or how they connect to the network. Only one security solution is needed, and it must protect all remote users. It encompasses almost everything, from threat prevention to content filtering, zero-trust network access, and even zero-trust network access. In addition, it protects laptops, cellphones, and tablet computers. One policy engine and analytics platform that only needs to be configured once and can then be used universally. Both your users and your data have migrated beyond the confines of your network’s perimeter and into the cloud. The cloud-first strategy utilized by Wandera guarantees a unified and faultless security experience for users located in remote locations. Additionally, it does not confront the difficulties of converting historical designs to the new style of working that is prevalent nowadays.
5. FortiClient
Endpoint security has many layers, including behavior-based analysis, to guard against both known and new threats. Real-time monitoring of your whole global software inventory is possible at all times. Your worldwide software inventory is viewable to you at any time and from any location. FortiClient is an endpoint protection solution that is supplied via the cloud and is designed for use by small and medium-sized enterprises. A comprehensive endpoint protection platform that offers protection from threats of the next generation, insight into all of your hardware and software inventories, and management over the entirety of your security network.
Locate compromised hosts on your attack surface and take corrective action on them. The Fortinet Security Fabric relies heavily on FortiClient as a fundamental building block. Endpoints are included in the fabric so that advanced attacks may be thwarted and early detection can take place. Real-time reporting is used for a variety of security events, including the discovery of zero-day malware, botnets, and vulnerabilities.
GlobalProtect Review & Alternatives FAQs
How does GlobalProtect work?
GlobalProtect uses VPN technology to create a secure tunnel between the user's device and the enterprise network, encrypting all traffic to protect against cyber threats.
What types of devices and operating systems does GlobalProtect support?
GlobalProtect supports a wide range of devices and operating systems, including Windows, macOS, iOS, Android, and Linux.
What are some key features of GlobalProtect?
Key features of GlobalProtect include user identification and authentication, device management, network segmentation, and threat prevention.
How does GlobalProtect compare to other VPN solutions?
GlobalProtect is known for its ease of use, scalability, and customization, and includes advanced features such as network segmentation and threat prevention. It is also known for its high performance and reliability.
What are some popular alternatives to GlobalProtect?
Some popular alternatives to GlobalProtect include Cisco AnyConnect, Fortinet FortiClient, and OpenVPN.
How can businesses get started with GlobalProtect?
Businesses can get started with GlobalProtect by purchasing a license from Palo Alto Networks, deploying the software on their network, and configuring the solution to meet their specific business needs.
What types of support are available for GlobalProtect?
Palo Alto Networks offers a range of support resources for GlobalProtect, including technical support, online documentation, and a knowledge base.