User behavior analytics can be quite complex, but it doesn’t have to be. Below, I’ll simplify how it works, touch on some best practices, and share some tools and tips to help you get it set up quickly for yourself.
What Is User Behavior Analytics?
User Behavior Analytics (UBA) focuses on tracking and analyzing user actions within a system. It helps identify patterns that may indicate security threats, such as unusual login times or access to sensitive data. UBA uses machine learning to detect anomalies by comparing current behavior to established baselines.
This technology is essential in identifying insider threats and compromised accounts. UBA provides deeper insights into user activity, enabling organizations to enhance their security measures.
How Does User & Entity Behavior Analytics Work?
UEBA can be quite complex, but it can essentially be broken down into five steps:
- Data Collection User and Entity Behavior Analytics start by collecting data from various sources within an organization. This includes logs from servers, applications, and network traffic. Data is gathered continuously to ensure comprehensive monitoring. The more data sources integrated, the more accurate the analysis. Effective data collection is crucial for identifying normal and abnormal behavior patterns. Without thorough data collection, the system’s ability to detect threats is compromised.
- Establishing Normal Behavior Patterns Once data is collected, UEBA establishes baseline behavior patterns. These patterns represent typical user and entity actions over time. Machine learning algorithms analyze the data to define what is considered normal. This includes login times, access to specific files, and usage patterns. Establishing these baselines is essential for detecting anomalies. The more accurate the baseline, the better the system can identify potential threats.
- Anomaly Detection With baseline patterns in place, UEBA continuously monitors for deviations. Anomalies are identified when behavior significantly diverges from the established norm. For example, an unusual login time or accessing sensitive data unexpectedly. Machine learning algorithms play a key role in spotting these irregularities. Detecting anomalies quickly is critical for mitigating potential security risks. The system flags these anomalies for further investigation.
- Data Analysis Detected anomalies are then analyzed in-depth to assess their severity. UEBA uses advanced analytics to determine the nature of the deviation. This step involves correlating different data points to understand the context. For example, analyzing if unusual access is due to a legitimate need or a potential threat. Detailed analysis helps in accurately classifying the threat level. Proper analysis ensures that real threats are prioritized, and false positives are minimized.
- Real-Time Alerts When a potential threat is identified, UEBA systems generate real-time alerts. These alerts notify security teams immediately about suspicious activities. The system provides detailed information about the anomaly for quick assessment. Real-time alerts are crucial for prompt response to security threats. Delays in detection can lead to significant damage, so immediate alerts are vital. Security teams can then take necessary actions to investigate and mitigate the threat.
- Continuous Improvement UEBA systems continuously learn and adapt to new data and threats. Machine learning algorithms are refined over time to improve accuracy. This ongoing improvement helps in better detecting evolving threats. Feedback from security teams is also used to enhance the system. Continuous improvement ensures that UEBA remains effective in identifying and mitigating risks. Adapting to new challenges is essential for maintaining robust security.
What is an Example of User Behavior Data?
User behavior data encompasses various actions users take within a system. For example, login records show when and from where users access their accounts. This data can highlight unusual login times or locations that might indicate a compromised account. File access logs are another example, recording which files users view or edit. Analyzing these logs can uncover unauthorized access to sensitive information.
Additionally, application usage data tracks how users interact with different software. This can help identify irregular usage patterns that deviate from normal behavior. Email activity, including sending, receiving, and forwarding emails, is also monitored. Abnormal email activity can indicate phishing attempts or other security breaches.
UEBA Use Cases
User and Entity Behavior Analytics has several important use cases in enhancing security. One primary use is detecting insider threats. By monitoring user behavior, UEBA can identify when an employee is accessing data they shouldn’t, which could indicate malicious intent or a compromised account.
Another key use case is identifying compromised accounts. UEBA detects anomalies in login patterns, such as unusual times or locations, signaling potential account hijacking. This helps in quickly securing accounts before significant damage occurs.
UEBA also aids in spotting advanced persistent threats (APTs). By analyzing entity behavior, it can identify long-term, sophisticated attacks that traditional security measures might miss. This proactive approach is crucial for early threat detection and mitigation.
Lastly, UEBA enhances compliance monitoring. It ensures that users adhere to policies and regulations by tracking and reporting deviations. This helps organizations maintain compliance with industry standards and avoid penalties.
User Behavior Analytics Challenges
- Data Volume and Variety One of the biggest challenges in User Behavior Analytics (UBA) is managing the sheer volume and variety of data. Organizations generate massive amounts of data from various sources, which can be overwhelming. Integrating these diverse data formats requires significant effort and advanced tools. Ensuring consistent data quality across all sources is crucial for accurate analysis. Effective data management strategies are essential to handle the complexity and scale of the data involved.
- High Rate of False Positives UBA systems often struggle with a high rate of false positives. These systems might flag normal activities as suspicious, creating unnecessary alerts. This can overwhelm security teams and lead to alert fatigue. When teams become desensitized to alerts, they might miss genuine threats. Fine-tuning the system to reduce false positives while still detecting real threats is a challenging and ongoing process.
- Privacy Concerns Privacy concerns are a significant challenge for UBA. Monitoring user behavior involves collecting sensitive data, which raises privacy issues. Organizations must comply with data protection regulations to maintain user trust. Implementing robust data governance and anonymization techniques is essential. Balancing security needs with privacy rights requires careful planning and execution.
- Need for Specialized Skills Effectively managing a UBA system requires specialized skills. Expertise in data analysis, machine learning, and cybersecurity is crucial for success. Finding and retaining professionals with these skills can be difficult and expensive. Investing in ongoing training and development is essential to build a capable security team. Without skilled personnel, the effectiveness of UBA systems is greatly diminished.
- Evolving Threat Landscapes The constantly evolving nature of cyber threats adds complexity to UBA. Threat actors continually develop new tactics and techniques to bypass security measures. UBA systems must adapt to these changes to remain effective. Keeping the system updated and responsive to emerging threats is a continuous challenge. Regular updates and continuous improvement are necessary to maintain an effective UBA system.
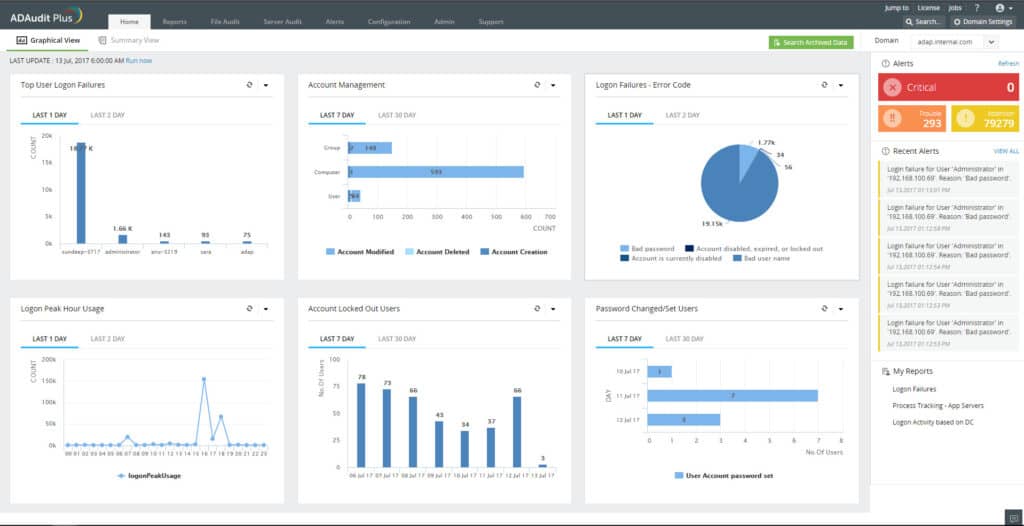
ManageEngine ADAudit Plus helps administrators overcome common challenges associated with implementing UEBA by offering seamless data integration from various sources, ensuring comprehensive coverage and accurate threat detection.
Its advanced machine-learning algorithms reduce false positives, making anomaly detection more reliable and efficient. The platform prioritizes user-friendliness with an intuitive interface and customizable reports, reducing the learning curve and enhancing productivity.
Additionally, ADAudit Plus provides robust support and training resources, equipping teams with the necessary skills to maximize the platform’s potential and maintain compliance with privacy regulations.
How To Choose The Right User Behavior Analytics Platform
- Data Integration Capabilities When choosing a User Behavior Analytics (UBA) platform, start by evaluating its data integration capabilities. The platform must seamlessly collect data from various sources like servers, applications, and network logs. Comprehensive data coverage ensures a holistic view of user and entity behavior. The platform should support multiple data formats and sources, making integration effortless. Check if it offers pre-built connectors for popular data sources to simplify the setup process. Effective data integration is crucial for accurate analysis and threat detection.
- Machine Learning and Anomaly Detection The core of a robust UBA platform lies in its machine learning and anomaly detection capabilities. Advanced algorithms help establish normal behavior patterns and identify deviations. Look for platforms that use machine learning to adapt and improve over time. Real-time monitoring is essential for prompt detection and response to threats. The platform should provide detailed insights into detected anomalies to help security teams assess risks accurately. An effective anomaly detection system minimizes false positives and ensures reliable threat identification.
- User-Friendliness User-friendliness is another crucial factor in selecting a UBA platform. The platform should have an intuitive interface that makes it easy to navigate and use. Clear, actionable insights are vital for enabling security teams to respond quickly to threats. Look for features like customizable dashboards and reports to suit your specific needs. User training and ease of use can significantly impact the platform’s effectiveness. A user-friendly platform reduces the learning curve and enhances overall productivity.
- Scalability Scalability is essential, especially for growing organizations. The UBA platform should handle increasing data volumes without compromising performance. Check if the platform supports scaling out by adding more resources as needed. It should accommodate expanding infrastructure and evolving security needs. A scalable platform ensures long-term viability and effectiveness. Ensuring the platform can grow with your organization prevents the need for frequent replacements or upgrades.
- Support and Training Resources Lastly, assess the platform’s support and training resources. Comprehensive support can significantly enhance your security team’s ability to use the platform effectively. Look for vendors that offer robust customer support, including 24/7 assistance. Training resources such as documentation, tutorials, and webinars are essential for maximizing the platform’s potential. Evaluate the quality and availability of these resources to ensure your team is well-equipped. Strong support and training resources help you get the most out of your UBA platform and improve your security posture.
ManageEngine ADAudit Plus helps administrators easily implement User and Entity Behavior Analytics by providing comprehensive real-time monitoring and alerting for Active Directory activities. It collects detailed logs from various sources, offering a holistic view of user behavior.
The platform’s intuitive interface and customizable reports simplify the analysis of complex data, making it accessible even for those with limited technical expertise. The platform’s advanced machine learning algorithms detect anomalies and potential threats, enhancing security with minimal manual intervention, making it viable for both small and expanding organizations. You can register for a 30-day free trial.
User and Entity Behavior Analytics Best Practices
- Comprehensive Data Collection Ensure your User and Entity Behavior Analytics (UEBA) system collects data from all relevant sources. This includes logs from servers, applications, and network traffic. Comprehensive data collection is crucial for establishing accurate behavior baselines. Integrate diverse data formats and sources to get a holistic view. Missing data points can lead to inaccurate analysis and missed threats.
- Regular System Tuning Regularly tune your UEBA system to reduce false positives and improve accuracy. Adjust thresholds and refine machine learning models based on new data and insights. Periodic reviews help in adapting to evolving threats and changing organizational behavior patterns. Continuous tuning ensures the system remains effective over time. This proactive approach minimizes alert fatigue and enhances threat detection.
- Focus on Privacy and Compliance Prioritize privacy and compliance when implementing UEBA. Ensure data collection and analysis practices adhere to relevant regulations like GDPR or HIPAA. Use anonymization and data masking techniques to protect sensitive information. Clear policies and transparent practices build user trust and meet legal requirements. Balancing security needs with privacy rights is essential for sustainable UEBA deployment.
- Invest in Training and Skill Development Invest in training your security team to effectively use the UEBA system. Provide ongoing education on data analysis, machine learning, and cybersecurity. Well-trained personnel can better interpret alerts and take appropriate actions. Regular training updates ensure the team stays current with new features and evolving threats. Skilled users maximize the system’s potential and improve overall security posture.
- Continuous Improvement and Updates Commit to continuous improvement and regular updates for your UEBA system. Cyber threats are constantly evolving, and the system must adapt to remain effective. Implement updates to address new vulnerabilities and enhance features. Encourage feedback from users to identify areas for improvement. Continuous improvement ensures the system stays robust and responsive to emerging threats.